Archive for the ‘Blog’ Category
End of an Era for On-Premises Phone Systems
The traditional on-premises telephony market has been in significant decline for some time now, driven by a global migration to cloud-based Voice over Internet Protocol (VoIP) systems and the impending shutdown of legacy analogue networks.
In the UK and many other parts of the world, the traditional Public Switched Telephone Network (PSTN) and ISDN lines, which on-premises systems rely on, are being phased out and are set to be fully switched off by the end of January 2027. This makes a transition to digital, IP-based solutions a necessity, not just an option.
The Main Drawbacks of On-Premises Phone Systems
- Vulnerability to Cyber Threats: While many organizations equate on-site equipment with greater control, on-premises phone systems can introduce significant cybersecurity vulnerabilities if not proactively maintained. Legacy hardware and outdated software often lack modern security protocols, making them attractive targets for threat actors.
- Transitioning to cloud-based telephony solutions not only enhances scalability and resilience but also ensures continuous security updates, centralized monitoring, and compliance alignment all of which are critical in today’s threat landscape.
- Ongoing Maintenance Costs: On-premises PBX deployments often appear cost-effective at first glance, but they demand substantial upfront investment in hardware, cabling, and specialized IT support. As these systems age, maintenance costs escalate driven by the need to replace legacy components, apply firmware updates, and resolve hardware faults that disrupt service continuity.
- Unlike cloud-based alternatives, on-premises setups lack built-in scalability and often require manual intervention for even routine changes. This not only strains internal resources but also delays responsiveness in fast-moving business environments.
- Limited Scalability: In today’s fast-paced business environment, agility is everything. Yet on-premises PBX systems often struggle to keep up with rapid growth or seasonal spikes in call volumes. Scaling up typically requires purchasing additional phone ports — and in many cases, upgrading the entire PBX hardware to support higher capacity. Even short-term increases in demand can trigger disproportionate capital outlays, locking businesses into costly infrastructure for temporary needs. This rigidity hampers responsiveness and puts smaller or mid-sized organizations at a disadvantage compared to competitors who’ve embraced cloud-based VoIP solutions.
- Hosted VoIP based platforms offer ease of scalability, allowing businesses to add or remove lines instantly, without hardware constraints or long-term commitments. This flexibility allows the business to adapt quickly to market shifts, customer demands, and growth opportunities all while maintaining predictable costs.
- Lack of Flexibility and Mobility: Today’s workforce is fluid spanning home offices, client sites, and global time zones. Yet traditional on-premises phone systems are rooted in a static model, often lacking the mobility features that modern teams rely on. Remote employees frequently struggle to access company lines or voicemail outside the office, creating friction in daily operations. Enabling advanced call forwarding, mobile apps, or unified communications typically requires costly add-ons or complex configurations if it’s possible at all. These limitations not only reduce productivity but also undermine flexible work policies that are now essential for attracting and retaining top talent.
- Cloud-based telephony platforms offer seamless access from any device, anywhere, empowering teams to stay connected, responsive, and collaborative without infrastructure constraints. For organizations embracing hybrid work, mobility isn’t a luxury, it’s a strategic imperative.
- The Upgrade Dilemma: In a competitive landscape, standing still is falling behind. Yet on-premises phone systems make it difficult to evolve. Adding modern features like voicemail-to-email, call analytics, or video integration often requires on-site installations, software patches, and specialized technical support. In many cases, outdated hardware must be replaced entirely just to enable a single new capability. These upgrade hurdles lead to higher costs, longer downtimes, and delayed innovation leaving businesses stuck with obsolete tools that can’t keep pace with customer expectations or operational needs.
- In contrast, cloud-based VoIP platforms deliver continuous innovation through automatic updates, modular feature rollouts, and seamless integrations, without the need for disruptive infrastructure changes. For organizations focused on agility and future-readiness, the choice is clear.
- Resilience Risks: On-premises phone systems are physically tethered to a single location, making them vulnerable to local disruptions such as power outages, fires, or natural disasters. If the PBX server or critical hardware is compromised, phone operations can grind to a halt indefinitely, leading to lost revenue, missed opportunities, and diminished customer trust. Without costly backup infrastructure, most on-premises setups lack the redundancy needed to recover quickly.
- For organizations prioritizing uptime and disaster recovery, cloud-hosted systems provide a strategic advantage: built-in resilience, faster recovery, and peace of mind.
What now for On-Premises Phone Systems
For many businesses, on-premises phone systems have been a reliable and familiar solution for communication needs. However, the telecommunications landscape is rapidly evolving, and cloud-based solutions are becoming increasingly popular.
What This Means for Your Business
If your business currently uses an on-premises phone system, you should already be making plans for the inevitable move to VoIP based systems. Here are a few things to consider:
- Evaluate your options: There are a wide range of cloud-based phone systems available on the market. Take some time to research your options and find a solution that meets the specific needs of your business.
- Consider the costs: Cloud-based phone systems typically have a lower upfront cost than on-premises systems. However, there are also ongoing monthly fees to consider.
- Plan for migration: Migrating to a new phone system doesn’t have to be a complex process. With proper planning and a clear strategy for migrating your users and data to the new system there is no reason for the move to be anything other than business as usual.
- Flexibility and Mobility: Cloud systems allow users to make and receive calls from anywhere on a variety of devices (smartphones, laptops, VoIP handsets), which is better suited to modern business needs than the rigid infrastructure of on-premises systems.
Why wait for disruption?
Speak to one of our experts today and explore how a modern telephony upgrade can transform your operations. Whether you’re scaling, embracing hybrid work, or streamlining costs, we’ll help you move beyond legacy limitations and into a more agile, resilient future.
Let’s make your communications smarter, faster, and built for what’s next.
02894485113
Windows 10 End of Life on 14 October 2025
🚨 One Week to Go: Windows 10 End of Life on 14 October 2025 🚨
The countdown is nearly over. In just one week, Microsoft will officially end support for Windows 10. This means no more security updates, no more patches and no more technical assistance. Systems that remain on Windows 10 will be exposed to increased risk and potential disruption.
If you have not yet started your upgrade, now is the time to act. Waiting any longer could leave your organisation vulnerable.
The Outsource Group Customer Engagement team is ready to help you transition smoothly and securely. Reach out today to discuss your options and avoid last-minute complications.
📩 Get in touch directly to get started:📞 028 9448 5112 ✉️ info@osgroup.co.uk 🌐 www.osgroup.co.uk
Strengthening Cyber Resilience with Tabletop Exercises
In today’s threat landscape, cyber resilience is more than just having the right technology — it’s about ensuring your people and processes are ready to respond. At ANSEC IA, part of Outsource Group, we’ve been helping organisations across the UK and beyond build stronger cybersecurity foundations for over 18 years.
One of the most effective ways to prepare for cyber incidents is through Cyber Tabletop Exercises — realistic, risk-based simulations that test your team’s ability to respond under pressure.
What Are Cyber Resilience Tabletop Exercises?
Tabletop exercises simulate real-world cyber incidents in a controlled environment. They help organisations assess their readiness, improve decision-making and strengthen communication across departments.
Key Benefits of Tabletop Exercises:
✅ Identify vulnerabilities before they become breaches
🧠 Improve crisis response and decision-making under pressure
🤝 Enhance cross-team coordination and communication
📋 Support regulatory compliance and build stakeholder confidence
💼 Minimise financial and operational impact through preparedness
More Than Just Simulation: Forensics and Sector Expertise
Alongside our tabletop services, ANSEC IA offers digital forensic capabilities to support complex investigations. Our experts provide clarity, accountability and evidence-based insights when it matters most.
We bring deep sector knowledge across:
- Criminal Justice
- Health
- Pharmaceuticals
- Utilities
This allows us to tailor exercises and forensic support to your specific regulatory and operational needs.
Build Confidence Through Preparedness
Cyber resilience isn’t just about reacting — it’s about being ready. Tabletop exercises help your organisation move from reactive to proactive, ensuring your team knows what to do when the unexpected happens.
📞 Call us: 028 9448 5112
✉️ Email: info@osgroup.co.uk
🌐 Visit: www.osgroup.co.uk
Think You Can Spot a Phishing Email? Think Again.
Phishing attacks are no longer easy to spot. Gone are the days of obvious spelling mistakes and suspicious links. Today’s phishing emails are polished, professional and alarmingly convincing — making it harder than ever to tell what’s real and what’s a threat.
How to Spot a Phishing Email in 2025
Cybercriminals are evolving their tactics. Here’s how phishing emails are becoming more sophisticated:
📧 Perfect Grammar and Branding
Modern phishing emails mimic corporate tone, use accurate logos and even include familiar names — often from spoofed or compromised email addresses — to appear legitimate.
🔗 Links That Look Trustworthy
Attackers now send phishing emails via platforms we trust, such as Microsoft 365, Google or Amazon. They may even chain together multiple services to mask their activity and avoid detection.
📨 Sender Addresses That Look Spot-On
Phishing messages often come from domains that closely resemble real ones. Some attackers use compromised business accounts or register lookalike domains to trick recipients.
What Can You Do to Stay Safe?
Phishing is no longer just an email problem. Here are some essential tips to protect yourself and your business:
🔐 Highlight the Sophistication
Don’t rely on grammar or branding to spot phishing. Many emails now look perfect — even to trained eyes.
📱 Watch Out Beyond Email
Phishing can come via SMS, QR codes, social media messages and even direct messages on platforms like Microsoft Teams.
☁️ Trusted Platforms Can Be Abused
Just because an email comes from a known service doesn’t mean it’s safe. Always verify before clicking.
🛡️ Use Technology to Your Advantage
Enable multi-factor authentication (MFA) wherever possible. Use unique, complex passwords and consider moving to phishing-resistant authentication methods.
📞 Verify Requests
Always double-check sensitive requests — especially those involving payments or changes to routine processes. Use a known, separate channel like a phone call to confirm.
🧠 Stay Sceptical
Expect the unexpected. Question everything. Never act hastily on digital prompts, no matter how urgent they seem.
Protect Your Business from Phishing Attacks
At Outsource Group, we help businesses stay secure with tailored cyber security solutions, including:
- Phishing awareness training
- Email security tools
- Multi-factor authentication setup
- Endpoint protection and monitoring
📞 Call us: 028 9448 5112
✉️ Email: info@osgroup.co.uk
🌐 Visit: www.osgroup.co.uk
Cybersecurity Basics for Small Businesses: 5 Tools to Boost Your Defences
Cyber threats are on the rise — and small businesses are increasingly in the crosshairs. According to the NCSC Cyber Security Breaches Survey 2024, nearly 50% of UK businesses and 32% of UK charities experienced cyber incidents last year.
Why Are Small Businesses Targeted?
Small and medium-sized businesses (SMBs) are often seen as easy targets for cybercriminals. Here’s why:
- There are more of them – creating a larger attack surface
- They often lack robust cyber security measures
- They can be used as entry points in supply chain attacks
But here’s the good news: you don’t need a huge budget to improve your cyber resilience. With the right tools and a consistent approach, you can protect your business from common threats.
5 Essential Cybersecurity Tools for SMBs
1. Endpoint Detection & Response (EDR) 🖥️
EDR solutions automatically detect and isolate threats across your devices. This means fewer sleepless nights for your IT team and faster response times.
2. Password Manager 🔐
Strong passwords are essential, but managing them can be a hassle. A password manager simplifies this and often integrates with multi-factor authentication (MFA) for added security.
3. Employee Cyber Awareness Training 🎓
Your team is your first line of defence. Regular training on phishing, social engineering and safe browsing can prevent costly breaches.
4. Patch Management 🧩
Outdated software is a common vulnerability. Automated patch management ensures your systems stay up to date without manual effort.
5. Maximise Existing Subscriptions 📦
Already using Microsoft 365 or Google Workspace? These platforms include built-in security tools — make sure you’re using them to their full potential.
Cybersecurity Doesn’t Have to Be Complex
Start small, stay consistent and build a culture of security within your business. Even basic measures can make a big difference.
How to Stay Safe on Public Wi-Fi: Simple Tips to Protect Your Data
Public Wi-Fi is incredibly convenient — whether you’re working from a café, travelling, or simply browsing while out and about. But it also comes with risks. Cybercriminals often target unsecured networks to intercept sensitive information such as passwords, financial details and personal data.
In this post, we’ll share practical tips to help you stay safe when using public Wi-Fi, and explain how Outsource Group can support your business with secure connectivity solutions.
Why Public Wi-Fi Can Be Risky
Public networks are often unencrypted and accessible to anyone, making them a prime target for cyber threats. Common attacks include:
- Man-in-the-Middle (MitM) attacks
- Fake Wi-Fi hotspots
- Data interception and theft
Without proper precautions, your device and data could be exposed.
5 Easy Ways to Stay Secure on Public Wi-Fi
1. Use a VPN (Virtual Private Network) 🛡️
A VPN encrypts your internet connection, keeping your browsing activity private and secure — even on open networks.
2. Avoid Logging Into Sensitive Accounts 🚫
Try not to access banking apps, work emails or confidential documents while connected to public Wi-Fi.
3. Turn Off Automatic Wi-Fi Connections 📴
Disable settings that allow your device to connect to networks automatically. This helps prevent accidental connections to unsafe hotspots.
4. Use HTTPS Websites Only 🌐
Always check that the websites you visit are secure. Look for “https://” in the URL and a padlock icon in the browser.
5. Forget the Network After Use ❌
Manually disconnect and remove the Wi-Fi network from your saved list to avoid automatic reconnection in the future.
Protect Your Business with Outsource Group
At Outsource Group, we help businesses stay secure with tailored connectivity solutions, including:
- Secure Wi-Fi as a Service
- Managed network support
- Expert cyber security advice
Let us take the stress out of staying connected — safely.
📞 Call us: 028 9448 5112
✉️ Email: info@osgroup.co.uk
🌐 Visit: www.osgroup.co.uk
Business Connectivity That Works as Hard as You Do
In today’s fast-paced digital world, reliable connectivity is no longer a luxury — it’s a necessity. At Outsource Group, we understand that your business needs telecoms and Wi-Fi solutions that are fast, secure and scalable. That’s why we deliver connectivity that works as hard as you do.
Tailored Telecoms Solutions for Modern Teams
Whether your team is in the office, working remotely or on the move, our telecoms services are built to keep everyone connected. With crystal-clear voice quality, flexible call plans and expert support just a phone call away, we make communication seamless and stress-free.
Key Benefits:
- 📞 High-quality voice calls
- 📱 Flexible and scalable call plans
- 🧑💼 Dedicated support from real people
Wi-Fi as a Service: Hassle-Free, Enterprise-Grade Connectivity
Managing your own network can be complex and time-consuming. With our Wi-Fi as a Service, we take care of everything — from site surveys and installation to ongoing monitoring and support. You get enterprise-grade Wi-Fi that grows with your business, without the upfront costs.
Why Choose Wi-Fi as a Service?
- 📶 Scalable and secure connectivity
- 🔒 Proactive monitoring and support
- 💼 No capital expenditure — just predictable monthly costs
Scalable. Secure. Supported.
At Outsource Group, we don’t believe in one-size-fits-all solutions. Our connectivity services are designed to adapt to your business needs, ensuring you stay productive, protected and prepared for growth.
✅ Scalable – Grow your network as your business expands
✅ Secure – Keep your data and communications protected
✅ Supported – Get help from real people, not bots
Ready to Simplify Your Connectivity?
Let’s make your telecoms and Wi-Fi simple, smart and stress-free. To find out how we can help your business stay connected:
📞 Call us: 028 9448 5112
✉️ Email: info@osgroup.co.uk
🌐 Visit: www.osgroup.co.uk
Is Your Device Infected? How to Spot Malware Before It’s Too Late
Malware is one of the most common cyber threats facing individuals and businesses today. It can silently infiltrate your device, steal sensitive data, slow down performance and compromise your online security. Recognising the early signs of malware infection is essential to protect your device and personal information.
In this post, we’ll explore the key symptoms of malware, how to respond effectively, and tips to keep your device safe.
What Is Malware?
Malware, short for malicious software, refers to any programme or code designed to harm, exploit or gain unauthorised access to a device or network. Common types include viruses, spyware, ransomware, trojans and adware.
6 Common Signs Your Device May Be Infected with Malware
If you notice any of the following issues, your device could be compromised:
1. Unexpected Slowdowns
Is your computer or phone suddenly running slower than usual? Malware often consumes system resources in the background, causing noticeable lag and poor performance.
2. Frequent Pop-Ups and Ads
Unwanted pop-ups, fake security alerts or ads urging you to “click here” are classic signs of adware or other malicious software.
3. Unexplained Data Usage
Spyware and other malware may send data back to cybercriminals, leading to abnormal spikes in your internet usage.
4. Unknown Programmes Installed
If you spot unfamiliar apps or software on your device that you didn’t install, it could be a sign of a malware infection.
5. Battery Draining Quickly
Malware running silently in the background can drain your battery much faster than normal.
6. Redirected Web Pages
If your browser keeps opening suspicious websites or your homepage has changed without your permission, malware may be altering your settings.
How to Remove Malware from Your Device
If you suspect your device is infected, take action immediately:
- Run a trusted antivirus or anti-malware scan
- Uninstall any unfamiliar or suspicious programmes
- Update your operating system and software regularly
- Avoid clicking on unknown links or downloading attachments from unverified sources
How to Prevent Malware Infections
Prevention is always better than cure. Here are some tips to keep your device safe:
- Use reputable antivirus software and keep it updated
- Enable firewalls and security settings
- Be cautious when downloading files or clicking on links
- Regularly back up your data
- Keep your operating system and apps up to date
Final Thoughts
Malware can be devastating if left unchecked, but by staying vigilant and knowing the warning signs, you can protect your device and personal data. Cyber threats are constantly evolving, so regular maintenance and awareness are key.
Cybersecurity Myth: “We’re too small to be targeted!”
Think your business is off the hacker’s radar? Think again. Small and medium-sized businesses (SMBs) are actually prime targets for cyber-attacks, often more so than large corporations. Why?
✅ There are simply more SMBs out there ✅ SMBs often have fewer cybersecurity resources ✅ Every business has valuable data—customer details, bank info, employee records.
Most attacks aren’t meticulously planned – hackers exploit weaknesses they stumble upon. Following basic cyber hygiene practices like NCSC Cyber Essentials or CIS Critical Security Controls IG1 can help close those gaps.
💡 Cybercriminals operate like businesses. If attacking your company is too much effort, they’ll move on. You don’t need an impenetrable fortress – just strong enough defenses to make your business a tougher target than the rest.
Stay vigilant. Stay protected. 🔒To find out how we can protect your business, contact us: 📞 028 9448 5112 ✉️ info@osgroup.co.uk 🌐 www.osgroup.co.uk
Outsource Sponsors Dromore Amateurs
🎉 Outsource Group is beaming with pride to be the front-of-shirt sponsors for the Dromore Amateurs 2017 Kids Team! ⚽ Their passion and teamwork are truly inspiring, and we are thrilled to support them on their football journey. 🌟
At Outsource, we believe in the power of sports to shape young minds and build strong communities. Outsource Groups sponsorship of the Dromore Amateurs 2017 Kids Team is a testament to our commitment to fostering talent and encouraging teamwork. We are incredibly excited to see these young athletes grow and succeed, both on and off the field.
Supporting Grassroots Football: Grassroots football is the foundation of the sport, and we are proud to play a part in nurturing the next generation of football stars. By sponsoring the Dromore Amateurs, we aim to provide these young players with the resources and opportunities they need to excel. From new kits to training equipment, our support ensures that the team can focus on what they do best – playing football and having fun.
Encouraging Teamwork and Sportsmanship: At Outsource, we value teamwork and sportsmanship, qualities that are essential both in sports and in the workplace. The Dromore Amateurs 2017 Kids Team exemplifies these values, and we are honored to support them. We believe that through sports, young people learn important life skills such as discipline, perseverance, and cooperation.
Looking Ahead to Future Victories: We are eagerly looking forward to cheering on the Dromore Amateurs in their upcoming matches. Their dedication and enthusiasm are truly inspiring, and we are confident that they will achieve great things. As proud sponsors, we will be there every step of the way, celebrating their victories and supporting them through challenges.
Go Dromore Amateurs! 💪👏
#ProudSponsors #GrassrootsFootball #Teamwork #FutureStars #Cybersecurity
High-Performance Strategies in Sport and Business
On Thursday, 21st November, the Outsource Group team had the pleasure of partnering with AC Events, Radius Vehicle Solutions Ireland, and BELTRAE PARTNERS LIMITED to host the “Winning Strategies: High-Performance Parallels in Sport and Business” lunch at the stunning Waterman. This event was a remarkable convergence of industry leaders and sports professionals, aimed at exploring the synergies between high-performance strategies in both fields.
Our dynamic guest speakers, Caroline O’Hanlon and Andrew Trimble, captivated the audience with their powerful insights. Caroline, a renowned sportswoman and business leader, shared her experiences on how discipline and teamwork in sports can translate into business success. Andrew, a former professional rugby player, discussed the importance of resilience and adaptability in achieving high performance. Their presentations seamlessly blended lessons from sport and business, providing valuable takeaways for all attendees.
The event was masterfully guided by our charismatic MC, Stephen Watson, who ensured the afternoon flowed smoothly and kept the audience engaged. It was an inspiring afternoon of networking, learning, and sharing strategies for success. Attendees had the opportunity to connect with like-minded professionals, exchange ideas, and gain new perspectives on achieving excellence in their respective fields.
We extend our heartfelt thanks to everyone who joined us and contributed to the success of this event. Your participation and enthusiasm made it a truly memorable experience. We look forward to hosting more events that bring together the best of sport and business to inspire and empower our community.


#WinningStrategies #HighPerformance #SportAndBusiness #Waterman #Networking
Outsource Welcomes Karl Ledwith
Outsource Group Welcomes Karl Ledwith to the Outsource Group
A warm welcome to Karl, the newest member of TeamOutsource, joining us as Sales Support as part of our Customer Engagement Team.
The entire Outsource Group extends wishes for a prosperous and fulfilling tenure.
At Outsource, we believe in fostering a dynamic and inclusive work environment where every team member can grow and succeed. We are committed to creating a workplace that values innovation, collaboration, and professional growth.
We are always on the lookout for talented individuals who share our passion for excellence. If you are curious about other roles within Outsource, we invite you to explore our careers page and join our team. We have a variety of exciting opportunities available across different departments, including sales, marketing, IT, and more. Whether you are just starting your career or looking to take the next step, we have something for everyone.
Visit our Careers, Jobs – Outsource Solutions (osgroup.co.uk) to see our live vacancies and learn more about what it’s like to work at Outsource. Joining our team means becoming part of a company that values your contributions and supports your professional development
Understanding Browser Notifications: What You Need to Know
Understanding Browser Notifications: What You Need to Know
What Are Browser Notifications? Browser notifications are alerts that websites can send to your browser. When you first visit a site offering these notifications, you’ll see a pop-up asking if you want to allow or block them. If you allow them, notifications can appear anytime, even when you’re not on the site. They’re often used for updates, social media interactions, and sales alerts. However, cybercriminals can exploit these notifications to steal your money and information. 🚨
How Do Cybercriminals Exploit Browser Notifications? Cybercriminals use two main methods to send malicious notifications:
Hijacking Legitimate Websites: They can take over a legitimate site and send fake notifications. 🕵️♂️
Tricking Users on Malicious Sites: They can create malicious sites that prompt you to allow notifications, often disguised as something else, like a video player. 🎥
Once they have access, they can:
💣Display excessive pop-ups, inappropriate content, or other disruptive material to hold your system hostage.
🛑Send malicious ads (malvertising) to spread malware or steal your information.
🦠Include malicious files in notifications that, when clicked, download malware to your system.
Tips to Stay Safe:
🧠Think Before You Click: Always read and consider prompts before taking action.
🔒Check Permissions: Only allow notifications from trusted websites. Most browsers let you manage or block notifications globally.
🔄Keep Software Updated: Ensure your browser and other software are up-to-date with the latest security patches. Enable automatic updates for convenience.
🛡️Stay vigilant and protect yourself from malicious browser notifications!
Want to learn how we can help your business by Understanding Browser Notifications and more? Get in touch with our Cybersecurity Experts and find out how Outsource Group can keep your data safe 📞 Tel: +44 (0)28 9448 5112 📧 Email: info@osgroup.co.uk or visit our services page Outsource Managed Security – Outsource Solutions to find out more about what we do.
What is Malvertising?
Tuesday (Cybersecurity) Tips 💻🔒 – What is Malvertising?
In today’s digital world, most websites you visit will feature some form of advertising, such as ad banners or embedded videos. These ads often grab your attention with bold claims, promotions, or promises of free products. Based on your browsing history, some ads are more likely to catch your eye! 👀
What is Malvertising? 🤔
Malicious advertising, or malvertising, is when cybercriminals use ads to spread malware or trick users into providing sensitive information. Clicking on a malicious ad while browsing a webpage might redirect you to a fake login page or retail site that requests your sensitive information. Some malvertising can even download harmful files onto your system. 🚨
How Do Cybercriminals Gain Access to Ads? 👾
Websites typically don’t choose who advertises on their pages. Instead, they use ad networks to manage advertisers, traffic, and payments. Cybercriminals exploit this system by tricking ad networks into believing they are legitimate advertisers. Once in, they use their ads to target unsuspecting users. 🎯
Remember, just because you are on a reputable, well-known website does not mean the ads are safe to click. ⚠️
Stay Safe from Harmful Ads: 🛡️
📢 Think Before You Click: If something seems too good to be true, it probably is. 🤨
📢 Stay Updated: Keep your device and browser security patches up-to-date. 🔄
📢 Use Ad Blockers: Installing a reputable ad blocker can help protect you from malvertising by preventing ads from being displayed. 🚫
Stay safe out there! 🛡️💻 cybersecurity digitaltips onlinesafety malvertising securityawareness
Outsource Group Joins the Movember Movement
There are some VERY fresh faces this morning as Outsource Group joins the Movember Movement. 11 of our team begin their month-long fundraising campaign as part of ‘Movember’ – a global initiative dedicated to changing the face of men’s health. By growing a moustache, they are helping to raise awareness and funds for critical issues like prostate cancer, testicular cancer, and mental health.
💼 Why It Matters:
Prostate Cancer: The second most common cancer in men worldwide.
Testicular Cancer: The most common cancer in young men.
Mental Health: Men are often less likely to seek help, leading to higher rates of suicide.
Our Movember Team is spearheaded by Damien Atkinson, who shared with us the devastating loss of his brother last year after he sadly took his own life. He bravely spoke of the impact of his loss, and reminded all of us at Outsource about the battle many men fight against Mental Health. His story resonated with so many of us and his openness is testament to the volume of the group he has organised to take part in this worthy fundraising event.
🚀 How You Can Help:
Donate: Support the cause by donating to the Outsource Teams fundraising link as they join the Movember Movement https://lnkd.in/e9UwKHnr.
Spread the Word: Share this post and encourage others to get involved.
We’ll be keeping you up to date with the ‘growth’ of the fundraisers (or lack of in some cases 😉) Please show your support for the guys by donating.
Together, we can make a difference. Let’s change the face of men’s health, one moustache at a time! 💪
30 Minute Spotlight: Senior Leadership Cybersecurity Awareness Webinar – The Hidden Threat To Your Business
We are thrilled to extend an invitation to our Cybersecurity Awareness Month Webinar – 30 Minute Spotlight: Senior Leadership Cyber Awareness – The Hidden Threat To Your Business
This cybersecurity awareness webinar is crafted to enlighten you on the critical importance of Senior Leadership and Cybersecurity Awareness. Join us to hear from two industry luminaries: Peter Leitch, Founding Partner of ANSEC IA and Terry Moore, CEO of Outsource Group. These trailblazers have revolutionized how businesses worldwide approach and manage cybersecurity threats. Don’t miss this opportunity to gain invaluable insights from the best in the field!
Peter Leitch is the Founding Partner of ANSEC IA, a specialist IT security consultancy established in 2007. Peter has built ANSEC IA into one of Northern Ireland’s leading cybersecurity firms, known for its exceptional reputation in both the public and private sectors. Peter’s expertise lies in improving the security posture of businesses globally, and he has been instrumental in shaping how companies understand and implement comprehensive security strategies.
Terry Moore is the CEO and founder of Outsource Group, a company he established in 2000. Under his leadership, Outsource Group has grown significantly, with offices in Antrim, Belfast, Dublin, and Edinburgh. Terry recognized early on that security was a critical issue for businesses, especially during the “Millennium Bug” scare, and has since been dedicated to enhancing cybersecurity measures for companies worldwide. His vision and leadership have earned Outsource Group numerous accolades, including the Best Medium-Sized Business in Northern Ireland.
Both Peter and Terry are highly respected figures in the cybersecurity industry, known for their innovative approaches and dedication to protecting businesses from evolving cyber threats.
Date: 22nd October 2024
Time: 2:10pm – 3.10pm
Where: Online
Save the date and join us for an afternoon cybersecurity awareness webinar where we hear how two influential security leaders navigate third party risk and AI in their business. Additionally, there will be a rare opportunity for a Q & A session with Peter Leitch and Terry Moore.
Please register now to confirm your participation and we will send you a placeholder for your diary.
We very much look forward to welcoming you.
Can’t attend? Get in touch to see how we can help Contact – Outsource Solutions (osgroup.co.uk)
Best regards,
The Outsource Group Team
Help Us Secure Our World this Cybersecurity Awareness Month
Help Us Secure Our World this Cybersecurity Awareness Month
October is Cybersecurity Awareness Month (CSAM), an international initiative that educates everyone about online safety and empowers individuals and businesses to protect their data from cybercrime. Even amidst large-scale data breaches and cyberattacks, Cybersecurity Awareness Month reminds everyone that there are simple, effective ways to keep yourself safe online, protect your personal data, and ultimately help secure our world.
Outsource Group is proud to be a Champion and support this online safety and education initiative this October.
The theme is Secure Our World! This initiative reminds us that there are simple actions we can take every day to protect ourselves, our families, and businesses from online threats.
CSAM focuses on the top four ways to stay safe online:
1. Use strong passwords and a password manager 🔑
2. Turn on multifactor authentication 🔰
3. Recognize and report phishing 🎣
4. Update software ⚙
Cybersecurity Awareness Month is led by the Cybersecurity and Infrastructure Agency (CISA) and the National Cybersecurity Alliance. For more information about ways to keep you and your family safe online visit https://lnkd.in/eU_sZX28 and https://lnkd.in/eYiABmx
For more information on how we can help reduce your cybersecurity risk Contact – Outsource Solutions (osgroup.co.uk)


Outsource Welcomes New Sales Manager Conor
Outsource is delighted to welcome New Sales Manager Conor Marken. Conor brings a wealth of experience and a fresh perspective to our team, and we are confident that he will play a pivotal role in driving our sales strategy forward. His expertise and enthusiasm make him a valuable addition to #TEAMOUTSOURCE.
Conor, we are delighted to have you on board and look forward to seeing you thrive in your new role. Your success is our success, and we are committed to supporting you every step of the way. Welcome to the team! 👏
At Outsource, we believe in fostering a dynamic and inclusive work environment where every team member can grow and succeed. We are always on the lookout for talented individuals who share our passion for excellence. If you are curious about other roles within Outsource, we invite you to explore our careers page and join our team. We have a variety of exciting opportunities available, and we would love to hear from you.
Visit our careers page to see our live vacancies and learn more about what it’s like to work at Outsource. Whether you are looking for a role in sales, marketing, IT, or any other department, we have something for everyone. Join us and be a part of a team that values innovation, collaboration, and professional growth.
Check out our careers page for more information: Careers, Jobs – Outsource Solutions (osgroup.co.uk)
Once again, a warm welcome to Conor Marken. We are excited to embark on this journey together and achieve great things. Here’s to your success and growth at Outsource! 🎉
#TEAMOUTSOURCE #WelcomeConor #JoinOurTeam #CareerOpportunities #SalesManager #NewBeginnings #SuccessAndGrowth
ANSEC IA and Outsource Macmillan Coffee Morning
ANSEC IA and Outsource Macmillan Coffee Morning
On the 18th of September, ANSEC IA staff members Ruth and Zara hosted a heart-warming Macmillan Cancer Support Coffee Morning for the staff of ANSEC IA and Outsource 💚. This event was dedicated to raising much-needed funds for an amazing charity that provides vital support to those affected by cancer.
Staff from both ANSEC and Outsource Group came together to enjoy delicious coffee ☕ and an array of tasty buns 🍰 🍪. It was a wonderful opportunity for everyone to gather, share a treat, and contribute to a very worthy cause. The atmosphere was filled with camaraderie and a shared sense of purpose, making the event both enjoyable and meaningful.
We are incredibly proud of Ruth and Zara for organizing such a successful event and grateful to all who participated and donated. Your contributions help Macmillan Cancer Support continue their essential work.
💚 About Macmillan Cancer Support 💚
Macmillan Cancer Support is dedicated to helping people living with cancer. They provide a comprehensive range of services, including emotional, practical, physical, and financial support. Their mission is to ensure that no one faces cancer alone, offering assistance at every step of the journey.
Remarkably, Macmillan Cancer Support is 98% funded by voluntary donations. This means that events like our coffee morning are crucial in enabling them to continue their invaluable work. Every donation, no matter how small, makes a significant difference in the lives of those affected by cancer.
If you would like to support this incredible cause, please consider making a donation. Your generosity can help provide the necessary resources and support for those in need. To donate, please visit: https://lnkd.in/eCWPunmP.
Thank you once again to everyone who joined us for the coffee morning and to those who have donated. Together, we can make a difference. Stay tuned for more updates on our community initiatives and events!
#MacmillanCancerSupport #CoffeeMorning #Fundraising #CommunitySupport #ANSECIA #OutsourceGroup #CharityEvent #CancerSupport #DonateNow #MakingADifference
Employee Spotlight – Jonny Weir
Employee Spotlight – Jonny Weir
Our employees are the backbone of the Outsource Group, consistently delivering exemplary service and security to our customers. Today, we’re excited to post the next in our “Employee Spotlight” series with Jonny Weir, where we highlight the incredible work our staff do to drive Outsources’ success.
🌟 Meet Jonny, our indispensable Senior Account Manager. He’s the joker of the pack and provides our customers with first class service, always on hand to make sure each of our valued customers are guided expertly on their digital and cyber security journey’s.
We took some time out to ask Jonny some questions on his vital role at Outsource Group in our Employee Spotlight series:
1. What is your job title?
Depends on the day, officially Senior Account Manager but when Sandra is in the office its official coffee maker.
2. How long have you worked for the Outsource Group?
I have been blessing Outsource Group with my presence for coming on 6 years.
3. What is your favourite thing about working for the Outsource Group?
It’s definitely not the people like everyone says!!!… only joking although the people are all great. I would have to say the customers I get to work with on a daily basis.
4. What was your motivation for picking the career you now work in?
Being totally honest I didn’t want to work in IT, but my careers teacher arrived at the house when I couldn’t get into tech to be a spark and told my mum she had enrolled me in an IT course, as a few people know I used to be an engineer (that’s the running joke but I was)
5. What is the most rewarding thing about your job?
Working for a company that stands by its staff. It also would be completing projects with customers and seeing how they have grown on both their digital and security journey.
6. Where do you see yourself in five years’ time?
Probably still asking Eamonn for that new coffee machine, still working with Outsource, driving to keep being the number one MSSP.
If you are interested in joining our team Visit our Careers Page, or contact us at recruitment@osgroup.co.uk with your details and we will contact you for a chat.
What is the difference between Phishing and SPAM?
Understanding the difference between phishing and spam is crucial for maintaining cybersecurity. Both are common types of unwanted emails, but they serve different purposes and pose different levels of threat.
Phishing
Phishing is a type of cyber-attack designed to deceive users into disclosing sensitive or valuable information, such as login credentials, financial details, or personal data. These attacks often come in the form of emails that appear to be from trusted organizations or individuals. Phishing emails typically create a sense of urgency or importance, urging recipients to act quickly to avoid negative consequences or to gain something valuable. For example, a phishing email might claim that your bank account has been compromised and prompt you to click a link to verify your identity. Once you click the link, you are directed to a fake website that looks legitimate, where you are asked to enter your sensitive information, which is then captured by the attackers.
SPAM
Spam, on the other hand, refers to unsolicited bulk emails that are usually commercial in nature. These emails are often sent to promote products, services, or websites. While spam emails can be annoying and clutter your inbox, they are typically not malicious. They do not usually attempt to steal your information or cause harm. Instead, they are more of a nuisance, trying to sell you something you may not be interested in. Examples of spam include promotional offers, advertisements, and newsletters that you did not sign up for.
Key Differences
- Intent: Phishing aims to steal sensitive information, while spam is generally intended to promote products or services.
- Threat Level: Phishing is malicious and poses a significant threat to your security, whereas spam is usually harmless but annoying.
- Tactics: Phishing emails often mimic trusted entities and create urgency, while spam emails are typically generic and sent in bulk.
Stay Safe
Remember, prompt reporting of suspicious emails can reduce the harm caused by cybercriminals. If you ever receive an email that seems suspicious, do not hesitate to ask for help or report it to your IT department.
For more information on how to protect yourself from phishing and spam, visit our website and learn about our comprehensive cybersecurity solutions Contact – Outsource Solutions (osgroup.co.uk)
Family Fun Day at Outsource HQ
Family Fun Day at Outsource HQ
On Saturday, August 24th, the Outsource Group hosted a spectacular Family Fun Day at our headquarters, celebrating everything family-related. From tiny paws to little feet, our staff, their families, and furry friends enjoyed a day brimming with delicious food and bouncy fun.
Our team works incredibly hard throughout the year, so it was only fitting to offer them some well-deserved rest and relaxation. We invited their cherished family members to Outsource HQ for a day filled with laughter, joy, and togetherness. The event featured a variety of activities, including bouncy castles, face painting, and games for all ages. We were even fortunate enough to have the rain stay away, allowing everyone to fully enjoy the sunny day! 🌞
The Family Fun Day was a fabulous event that truly highlighted the spirit and camaraderie of the Outsource family. It was heart-warming to see our team members bond with their loved ones and colleagues in such a relaxed and joyful setting. The smiles and laughter shared throughout the day were a testament to the strong sense of community and support that defines Outsource.
We believe that events like our Family Fun day at Outsource HQ, are essential for fostering a positive and inclusive work environment. By bringing our extended Outsource family together, we strengthen the connections that make our team so special. We are grateful to everyone who attended and contributed to making this day a memorable one.
For those interested in joining our dynamic and supportive team, we invite you to explore our careers page to see our live vacancies and learn more about what it’s like to work at Outsource. Whether you are looking for a role in sales, marketing, IT, or any other department, we have exciting opportunities available.
Thank you once again to everyone who made the Family Fun Day a success. We look forward to more events that celebrate our incredible team and their families.
Visit our careers page to see our live vacancies and learn more about what it’s like to work at Outsource. Whether you are looking for a role in sales, marketing, IT, or any other department, we have something for everyone. Join us and be a part of a team that values innovation, collaboration, and professional growth.
Check out our careers page for more information: Careers, Jobs – Outsource Solutions (osgroup.co.uk)
#FamilyFunDay #OutsourceGroup #TeamOutsource #Community #WorkLifeBalance #JoinOurTeam #CareerOpportunities #EmployeeEngagement #CompanyCulture #FamilyFirst
Darren Achieves AZ-900 Accreditation
Darren Achieves AZ-900 Accreditation
Let’s give a huge round of applause to Darren Irwin for achieving his AZ-900 Microsoft Azure Fundamentals Accreditation exam! 🎉 This is a stellar accomplishment, and we’re cheering him on as he sets his sights on the SC-900 Security, Compliance, and Identity Fundamentals accreditation. Darren’s dedication to continuous learning and professional development is truly inspiring, and we are proud to have him as part of the Outsource team.
Achieving the AZ-900 accreditation is no small feat. It demonstrates Darren’s solid understanding of Microsoft Azure fundamentals, including core Azure services, security, privacy, compliance, and trust. This certification is a testament to his hard work and commitment to staying at the forefront of technology. Best of luck, Darren – you’ve got this! 🚀
At Outsource, we believe in fostering a culture of continuous learning and professional growth. Darren’s achievement of the AZ-900 accreditation is a perfect example of how we support our team members in their pursuit of excellence. We provide ample opportunities for our employees to enhance their skills and advance their careers. Whether it’s through certifications, training programs, or hands-on experience, we are committed to helping our team members succeed.
Visit our careers page to see our live vacancies and learn more about what it’s like to work at Outsource. We have a variety of exciting opportunities available across different departments, including sales, marketing, IT, and more. Join us and be a part of a team that values innovation, collaboration, and professional growth. Just like Darren, who achieved his AZ-900 accreditation, you too can thrive in an environment that encourages continuous learning and development.
Check out our Careers, Jobs – Outsource Solutions (osgroup.co.uk) for more information and take the first step towards a rewarding career with Outsource. We look forward to welcoming more talented individuals to our team.
#TeamOutsource #AZ900 #MicrosoftAzure #Certification #ContinuousLearning #ProfessionalGrowth #JoinOurTeam #CareerOpportunities #Innovation #Collaboration #SuccessAndGrowth #DarrenAchievesAZ900Accreditation #OutsourceGroup
Employee Spotlight – Damien Atkinson
Employee Spotlight – Damien Atkinson
Our employees are the backbone of the Outsource Group, consistently delivering exemplary service and security to our customers. Today, we’re excited to post the next in our “Employee Spotlight” series with Damien Atkinson, where we highlight the incredible work our staff do to drive Outsources’ success.
🌟 Meet Damien, our indispensable Project Coordinator. Not only does he play a crucial role in our projects, but he also brings joy and laughter to the team. As a founding member of our social committee, S.P.A.R.K, Damien is always the first to step up and organize social and charity events.
We took some time out to ask Damien some questions on his vital role at Outsource Group:
1. What is your job title?
Jack of all trades, master of none! or Project Co-Ordinator
2. How long have you worked for the Outsource Group?
Seven and a half years.
3. What is your favourite thing about working for the Outsource Group?
PIZZA!!!, only joking…it’s the people for sure. I have made great friends for life throughout my Outsource journey. Also, the flexibility that is offered to you, nothing is ever a problem for Outsource, if you need to work from home at any time, it is always granted.
4. What was your motivation for picking the career you now work in?
I worked in retail for 13 years when I left education. Late 2016 was the moment I decided to explore other opportunities and thankfully I found Outsource. I initially joined Outsource as Sales Admin, then worked my way up to the Project Co-Ordinator role late 2019. I am passionate about pursuing a career in Project Management and hope to gain as much experience and qualifications in my current role to achieve that goal.
5. What is the most rewarding thing about your job?
Definitely working with so many of my colleagues from different departments. I am a very positive guy and love to make those around me smile/laugh. I can’t forget about the social events and especially the 20th anniversary of Outsource trip to Palma in September 2022. I have been very lucky to be working for such a great company. Bring on the 25th celebrations😊
6. Where do you see yourself in five years’ time?
Ideally, I hope I will have progressed with the project management goal and contributing to the company’s continued success.
*Damien is pictured with his family – his soon to be wife Natasha, twin girls Hannah & Chloe and little Eva, who Damien calls his ‘absolute life’.
Visit our careers page to see our live vacancies and learn more about what it’s like to work at Outsource. Whether you are looking for a role in sales, marketing, IT, or any other department, we have something for everyone. Join us and be a part of a team that values innovation, collaboration, and professional growth.
Check out our careers page for more information: Careers, Jobs – Outsource Solutions (osgroup.co.uk)
Employee Spotlight – Angela Smith
Employee Spotlight – Angela Smith
At Outsource Group, our employees are the heart and soul of our operations, consistently delivering exceptional service and ensuring our customers’ peace of mind. Today, we’re excited to unveil our second “Employee Spotlight” series with Angela Smith, where we celebrate the incredible individuals whose dedication and hard work drive our success.
🌟 Angela is the glue that binds together ANSEC IA (an Outsource Group company). As Office Manager of ANSEC IA, she is a confidante, facilitator, go getter and organisational whizz! (Not to mention she brings the cutest office dog to work for us all to get a cuddle!).
We took some time out to ask Angela some questions on her vital role at Outsource Group:
1. What is your job title?
Office Manager/PA.
2. How long have you worked for the Outsource Group?
Coming up to 1 year.
3. What is your favourite thing about working for the Outsource Group?
If you ask me what my favourite thing about working for Ansec IA is, that’s an easy one to answer: it’s their work ethos. The company not only encourages us to strive for excellence in our professional roles but also promotes a healthy work-life balance. They understand that personal life is as important as professional growth. This balance allows us to bring our best selves to work each day, fostering an environment of productivity and mutual respect. It’s more than just a workplace.
4. What was your motivation for picking the career you now work in?
At school, knowing what I wanted to be when “I grow up” wasn’t clear cut, so I picked subjects I enjoyed and was pretty good at i.e. maths, commerce, typing, art and languages. My mummy envisioned me as a Bi-lingual Interpreter, but I wasn’t convinced! During my “Work Experience” I was placed as a secretary’s assistant. I quickly realised that their role was central to the organisation and required knowledge in a wide variety of areas: HR, H&S, Finance, Legal, Marketing, Training & Development, Sales, Customer Service and Business Development and I’ve never looked back!
5. What is the most rewarding thing about your job?
The most rewarding aspect of my role lies in the variety and complexity of tasks that I handle. The organisational skills required to manage diverse responsibilities as well as the ability to pre-empt and provide solutions enhances my role significantly. Above all, acting as a confidante, facilitating open communication and mutual understanding, is truly rewarding.
6. Where do you see yourself in five years’ time?
I see myself constantly evolving in my role, making a meaningful impact, whilst still enjoying my work. I’m excited about the opportunities for self-improvement that lie ahead and the difference I can make in my workplace.
Alternatively, sailing around the Mediterranean (the crew that is, not me) with my four legged confidante “Koko”, and husband in tow, sipping Espresso Martinis – that would work too!
Visit our careers page to see our live vacancies and learn more about what it’s like to work at Outsource. Whether you are looking for a role in sales, marketing, IT, or any other department, we have something for everyone. Join us and be a part of a team that values innovation, collaboration, and professional growth.
Check out our careers page for more information: Careers, Jobs – Outsource Solutions (osgroup.co.uk)
The Role of DIGITAL FORENSICS
The Role of DIGITAL FORENSICS in Supporting Sensitive Investigations and Possible Litigation
As our exposure to technology continues to grow, the footprint we leave behind on digital devices grows with it. Consequently, during sensitive investigations, digital evidence is playing an increasingly important role in both civil and criminal investigations.
Our Digital Forensics team comprises industry-leading experts in the extraction and analysis of digital data to evidential standards acceptable by courts, tribunals, and other legal bodies. Our highly experienced team is trusted by private, public, and governmental bodies across numerous geographic regions.
The Role of Digital Forensics
Digital forensics involves the meticulous process of uncovering and interpreting electronic data. The goal is to preserve any evidence in its most original form while performing a structured investigation by collecting, identifying, and validating the digital information for the purpose of reconstructing past events. This is crucial in supporting sensitive investigations and possible litigation.
Our Services
We offer a comprehensive range of digital forensics services, including:
- Digital Forensic Analysis: Detailed examination of digital devices to uncover and analyze data.
- Forensic Readiness and Training: Preparing organizations to handle digital evidence effectively and providing training to staff.
- Data Preservation and Recovery: Ensuring that digital evidence is preserved in its original state and recovering lost or deleted data.
- Company Data Theft: Investigating incidents of data theft within organizations.
- Intellectual Property Theft: Protecting and investigating the theft of intellectual property.
- Employee Misconduct and Leavers: Investigating cases of employee misconduct and issues related to departing employees.
Our team is equipped with the latest tools and techniques to handle complex digital forensics cases. We ensure that all evidence is handled with the utmost care and integrity, maintaining a clear chain of custody to uphold its admissibility in legal proceedings.
If we can help your business or organization with any investigations or provide professional support and advice, please contact us at df@ansecia.com or visit our Digital Forensics page.
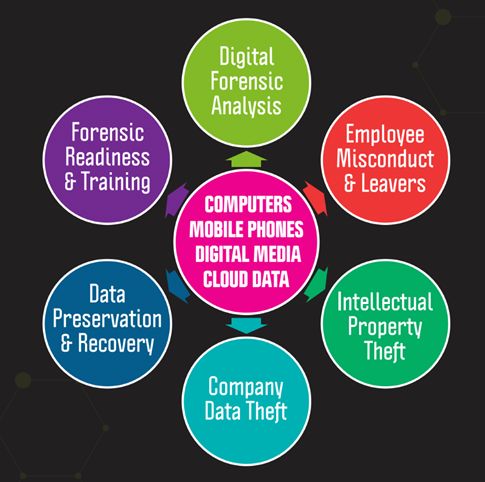
A diagram of the key aspects of Digital Forensics
If we can help your business or organisation with any investigations or professional support/advice, please contact us df@ansecia.com or visit Digital Forensics (ansecia.com)
(A diagram of The Role of Digital Forensics)
Has Your Business Upgraded It’s Human Firewall Yet?
Has Your Business Upgraded It’s Human Firewall Yet?
Your staff are the biggest security vulnerability to your business, with 91% of cyber-attacks originating from phishing emails.
Empowering staff with the tools and knowledge to recognise the signs of a phishing email needs to be an integral part of your wider security strategy. Strengthening your human firewall is key to hardening your overall security posture and protecting your business.
OUTSOURCE offer AI powered Security Awareness Training (SAT) and Phishing Testing for your staff. Our tools blend AI with an expansive and interactive content library, to deliver training with personalised content and simulated phishing, helping your staff recognise and remain vigilant to social engineering threats.
It is a fact that businesses who provide staff access to SAT and phishing simulation training are significantly less likely to compromise your business by clicking on malicious emails.



Features of our interactive training include:
– Access to a library of interactive training modules
– Regular staff enrolment in training
– Phishing simulations
– Phish alert button to notify your IT Dept. of a suspected phishing email
– Full Management Reporting on all activity
Our competitive pricing is based on per user per month and includes a dedicated Account Manager, available to help you with set up and ongoing management.
Whether with OUTSOURCE support or setting up your own constant internal training programmes, enhancing your human firewall expertise is a must for your business. If you would like further information or support get in touch and we can organise a demo for your business.
Contact Tara Leathem or Sandra Quinn or call on
for additional support and information.
The Value of a Table Top Exercise – “When Plans Meet Reality”.
The Value of a Table Top Exercise – “When Plans Meet Reality”
Having a plan to deal with any threat scenario is good, but testing that plan is even better. How will your organization and staff react under pressure? Are there gaps in your existing plans? Are roles and responsibilities clear enough? Only by experiencing a simulated exercise can you truly have reassurance that your plans are fit for purpose. Below is an outline of the value of a table top exercise – When Plans meet Reality”>
A table top exercise is a simulated, interactive exercise that tests the effectiveness of an organization’s emergency plans. It allows participants to discuss their roles during an emergency and their responses to a particular crisis scenario. This type of exercise is invaluable for identifying weaknesses in your plans and ensuring that everyone knows their responsibilities.
Benefits of Table Top Exercises
- Identify Gaps and Weaknesses: By simulating a real-life scenario, you can uncover gaps and weaknesses in your current plans that might not be apparent on paper.
- Clarify Roles and Responsibilities: These exercises help ensure that all team members understand their roles and responsibilities during a crisis.
- Improve Communication: Effective communication is crucial during any emergency. Table top exercises help improve communication channels and protocols.
- Build Confidence: Regularly testing your plans builds confidence among staff, ensuring they are prepared to handle real emergencies.
- Enhance Coordination: These exercises foster better coordination among different departments and teams, ensuring a unified response during a crisis.
ANSEC IA LTD: Your Partner in Crisis Preparedness
Since 2007, ANSEC IA LTD has been a leader in the IT Consultancy, Risk, and Governance space. We are experts in helping organizations prepare, document, and test crisis planning and preparedness. Our team of professionals can guide you through the process of conducting effective table top exercises, ensuring your organization is ready to face any threat scenario.
Get in touch with us for professional advice and support. We are here to help you build robust crisis management plans that stand up to real-world challenges.
For more information, visit Cyber Incident Response (ansecia.com) or our Security Vulnerability Threat Testing – Outsource Solutions (osgroup.co.uk) page.
#TableTopExercise #CrisisManagement #EmergencyPreparedness #RiskManagement #ANSECIA #OutsourceGroup
Outsource Awarded Nextwave Innovator Status by Palo Alto
Outsource Awarded Nextwave Innovator Status, by Palo Alto Networks
Outsource are delighted to have been awarded Nextwave Innovator status by Palo Alto Networks in recognition of our Security First approach, staff training and organisational expertise.
Palo Alto Networks is the world’s cyber security leader and a key Outsource Security Partner in our development plans. Our joint focus is to outpace cyber threats, so organizations can embrace technology with confidence. Palo Alto already provides next-gen cyber security to thousands of customers globally, across all sectors. We will leverage this partnership to enhance our existing security services and utilize their best-in-class cyber security platforms, industry-leading threat intelligence, and state-of-the-art automation systems.
Enhancing Security Services
By partnering with Palo Alto Networks, we aim to bring the most advanced and reliable cyber security solutions to our clients. Their cutting-edge technology and expertise will help us strengthen our security offerings, ensuring that our clients are protected against the latest threats. This collaboration allows us to provide comprehensive security solutions that are both robust and scalable, tailored to meet the unique needs of each organization.
Leveraging Industry-Leading Technology
Palo Alto Networks’ cyber security platforms are renowned for their effectiveness and innovation. By integrating these platforms into our services, we can offer unparalleled protection and peace of mind to our clients. Their industry-leading threat intelligence provides real-time insights into emerging threats, enabling us to stay ahead of cybercriminals and safeguard our clients’ digital assets.
State-of-the-Art Automation Systems
Automation is a key component of modern cyber security, and Palo Alto Networks excels in this area. Their state-of-the-art automation systems streamline security processes, reduce response times, and enhance overall efficiency. This means that our clients can focus on their core business activities, knowing that their security is in capable hands.
Looking Ahead
We are excited about the future and the potential this partnership holds. Look forward to more exciting announcements from Outsource as we continue our journey to becoming the Number 1 Security Focused Solutions and Services Provider in the market. Together with Palo Alto Networks, we are committed to outpacing cyber threats and empowering organizations to embrace technology with confidence.
Stay tuned for updates and join us on this exciting journey!
#CyberSecurity #PaloAltoNetworks #OutsourceGroup #SecurityPartner #NextGenSecurity #ThreatIntelligence #Automation #Innovation #Technology #SecuritySolutions #IndustryLeader #FutureReady #StayProtected #OutpaceThreats #EmbraceTechnology #SecurityFirst #NumberOneProvider #ExcitingAnnouncements #JoinOurJourney #OutsourceSecurity
For more information please visit Palo Alto MSSP & SOC Provider – Outsource Solutions (osgroup.co.uk)
Employee Spotlight – Cara McManus
Employee Spotlight – Cara McManus
Our employees are the back bone of the Outsource Group, always striving to give our customers exemplar service and security. Today, we’re pulling back the curtain on our “Employee Spotlight” series with Cara McManus, People & Culture as we shine a light on our staff and the fundamental work they do to make Outsource a success.
🌟 Cara’s Vital Role As our People & Culture Business Partner, Cara orchestrates the symphony of talent, weaving connections, nurturing growth, and harmonizing our workplace culture. She’s the compass guiding us toward a thriving, engaged team.
We took some time out to ask Cara some questions on her vital role at Outsource Group:
1. What is your job title?
People and Culture Business Partner
2. How long have you worked for the Outsource Group?
6 months 😊
3. What is your favourite thing about working for the Outsource Group?
Definitely the people. Their warmth and support have made my transition into this new role a breeze. Plus, who can resist our adorable office dog, Koko? 😊
4. What was your motivation for picking the career you now work in?
While studying for my marketing degree, I was working full time in a coffee shop as a supervisor dealing with day-to-day people management. This led me to pursue my CIPD Level 3 in People Practice to see if the interest went further, long story short it did and not long after I secured my first role in Manchester as HR Administrator. Fast forward 9 years, and here I am, still passionate about HR (and feeling a tad older).
5. What is the most rewarding thing about your job?
I think being able to be there for the good and bad times, from welcoming new hires to celebrating life’s big moments, or lending an ear when times are tough, I strive to maintain an open-door policy. After all, we all need a good rant sometimes!
6. Where do you see yourself in five years’ time?
In five years, I see myself continually learning and growing in my HR career because, as they say, “every day is a school day” 😊. And who knows, maybe I’ll add a few more fur babies along the way or perhaps I’ll be lucky enough to win the prize guy. 😉
* Cara is pictured enjoying some downtime at her favourite spot, the Four Winds Bar, with her favourite companion, Mila (her adorable cockapoo, also known as “The Child”).
Visit our careers page to see our live vacancies and learn more about what it’s like to work at Outsource. Whether you are looking for a role in sales, marketing, IT, or any other department, we have something for everyone. Join us and be a part of a team that values innovation, collaboration, and professional growth.
Check out our careers page for more information: Careers, Jobs – Outsource Solutions (osgroup.co.uk)
The importance of cyber resilience
At our recent Cyber Resilience event, we emphasised the famous boxing quote, “everyone has a plan until you are punched in the face,” highlighting the importance of readiness in dealing with cyber incidents.
In the same way athletes train and prepare for major sporting events, organisations need to be ready for their own “big event” in the form of a cyber incident. Achieving true cyber resilience requires a cohesive team and strategy to tackle the challenges posed by skilled adversaries, going beyond the notion of “letting IT deal with it.” This involves being prepared for the technical, organisational, and psychological aspects of incidents like ransomware attacks or data theft.
With the increasing reliance on technology, cyber-attacks have become all too common in today’s world, making it crucial for organisations to assess the impact of such incidents and determine how to contain the threat and expel the intruder from their networks. To ensure effective response capabilities, organisations must invest in resources and skills. This involves creating a comprehensive recovery plan based on best practices, employing the right personnel, and establishing fail-safe processes that can function even when key participants are unavailable. It’s important to understand that cyber resilience is not solely reliant on technological solutions – it requires a holistic approach encompassing people, processes, and technology.
However, being prepared is just the first step. To validate the effectiveness of your cyber resilience strategy, it is vital to have an intimate understanding of your business, its critical components, and how to restore them in the aftermath of an attack. To achieve this level of understanding, it is recommended to regularly and rigorously test your recovery plan. This testing helps to identify any gaps in the plan and ensure a smoother recovery process.
One highly effective method for enhancing the necessary skills and capabilities to achieve resilience is by conducting a cyber tabletop exercise. A cyber tabletop exercise is a simulated scenario that enables organisations to test and evaluate their preparedness and response capabilities in the event of a cyber incident or breach. It serves as a training tool for key stakeholders involved in managing and responding to cybersecurity incidents, including IT staff, executives, legal teams, and public relations representatives. The exercise takes place in a conference room or virtual environment and is based on realistic threats or previous incidents to provide a relevant and meaningful experience for the participating organisation.
During the exercise, participants assume specific roles and responsibilities, such as incident responders, incident commanders, legal advisors or media relations representatives. They are presented with a simulated event that unfolds gradually, and they must collaborate, make decisions, and take appropriate actions to respond to the evolving situation and adapt to new challenges that arise in a fast-moving environment.
The tabletop exercise serves several purposes:
- Testing response plans: By simulating real-world scenarios, organisations can identify gaps, weaknesses, and areas for improvement in their response strategies.
- Enhancing communication and coordination: The exercise promotes communication and coordination among different teams and stakeholders involved in incident response. It enables participants to understand each other’s roles, responsibilities, and decision-making processes, fostering better collaboration and coordination during a real incident.
- Identifying strengths and weaknesses: Through the exercise, organisations can identify their strengths, areas of expertise, vulnerabilities, and limitations in their incident response capabilities. This knowledge allows them to prioritise investments in training, external resources, and improvements to enhance their overall cybersecurity posture.
- Practicing decision-making: The exercise provides a safe environment for participants to practice making critical decisions under pressure. They can explore different response strategies, evaluate the potential consequences of their actions, and learn from their mistakes without real-world repercussions. It is better to fail during the exercise than in a real incident.
- Building familiarity with procedures: Tabletop exercises help participants become familiar with the incident response procedures, protocols, and tools that would be utilised during an actual cyber incident. This familiarity improves efficiency and effectiveness during a real incident, as responders are better prepared and more confident in their actions. It also helps external resources understand the organisation’s procedures and be better prepared to assist in an incident. This process strengthens the organisation’s cybersecurity posture and preparedness to handle real-world cyber threats.
Being aware of the latest cyber threats is a fundamental aspect of a good cyber resilience strategy. Understanding these threats enables organisations to better predict, detect, and respond to them. Conducting a tabletop exercise to test the ability to respond is critical for maintaining a high standard of cyber hygiene and informing the cybersecurity strategy.
A mature cybersecurity strategy that encompasses all aspects of threat identification, impact mitigation, and service recovery is essential. The current landscape in most organisations is characterised by technical dependency, and the rise of hybrid working models has blurred the boundaries of an organisation’s perimeter, making it harder to secure. The days of heavily investing in preventive security measures with the aim of blocking threat actors are no longer sufficient.
A paradigm shift is occurring in cybersecurity, with organisations embracing strategies such as “zero trust” that prioritise resiliency in the face of inevitable incidents. This shift necessitates partnering with strong cybersecurity providers who have the necessary technologies and knowledge to prevent or mitigate incidents while also understanding the organisation’s business context.
Ultimately, cyber resilience must be an integral aspect of a contemporary business strategy. With the increasing threats and sophistication of cyber-attacks, understanding your business’s assets, how technology supports business objectives, managing technology risk, focusing on recovery, and staying abreast of the latest threats are non-negotiable aspects.
Furthermore, it is essential to remember that a cyber resilience strategy is only as strong as its weakest link. Regular testing and investment in resources are paramount to ensure that your organisation remains strong in the face of cyber threats.
Phishing Attacks: An Escalating Threat to Businesses
Every day, there are 65,000 attempts to hack SMEs and among these, phishing attacks has emerged as the predominant method employed by malicious actors to illicitly obtain data, information, or funds.
Understanding Phishing
Phishing refers to deceptive tactics where perpetrators employ various platforms (such as emails, mobile messages, social media, phone calls, and texts) to mislead individuals into performing certain actions. These actions could be as simple as clicking a link, but they can lead to significant security breaches, allowing the attacker unauthorised access, theft of data, or even holding a company at ransom.
Strategies to Enhance Cybersecurity
To bolster defences against such intrusions, businesses can adopt several proactive measures:
- Training: Engage in continuous staff training and security awareness programs. This can be done in-house or via trusted IT partners, with the inclusion of regular simulated phishing tests.
- Anti-Virus Software: Ensure the use of reliable and frequently updated Anti-Virus solutions.
- Firewalls: Deploy both Desktop and Network Firewalls that are expertly set up and maintained.
- Browser Security: Always update browsers to incorporate the latest security patches, sealing any potential vulnerabilities.
- Pop-Ups: Always scrutinise pop-ups, even those that appear genuine.
- Site Security: Before interacting with a site, confirm its security credentials.
- Personal Information: Limit the amount of personal data shared online.
- Passwords: Adhere to robust password protocols, emphasising complexity and using combinations of random words.
- MFA (Multi-Factor Authentication): This should be a fundamental security provision.
- Think Before Clicking: If a message urges immediate action, pause and reflect. Feeling rushed often indicates potential deceit.
Remember, human error is inevitable. While these strategies offer substantial protection, it’s crucial to anticipate potential breaches. Thus, having a predefined response plan is indispensable. This ensures that in the event of a breach, appropriate actions are executed promptly, minimising further risks and disruptions.
To find out more about ways you can assess your vulnerabilities and improve your cyber security readiness email info@osgroup.co.uk
Will Cyber Insurance solve all your security problems?
In today’s age of digital transformation, cyber security threats have become a major concern for businesses. With an alarming number of cyber-attacks and data breaches, many companies have been turning to cyber insurance to protect themselves financially in the event of an attack. However, whilst cyber insurance can help businesses get back on their feet should a cyber-attack occur, it will not solve any security concerns a business may have nor prevent a data breach. And, as always with insurance of any kind, the question is whether it will pay out at all?
The cost of cyber insurance can vary depending on the size and type of business, as well as the level of coverage. But it can be a big investment, particularly for larger companies. Before investing in cyber insurance, it is worth taking time to figure out what financial impact a cyber-attack could have on your business and how you would be covered with your insurance. Some insurance policies do not cover some common cyber-attack incidents such as money lost through business email compromise fraud or a new type of cyber-attack that does not already exist on your insurance. Insurance companies are also putting in place a very high bar – some would say impossibly high – to meet the requirements of cyber insurance. Indeed, we are seeing more and more examples of insurance companies failing to pay out in the instance of cyber-attack on the basis that the customer hadn’t met some of the (often obscure) requirements.
Cyber insurance does have a role to play. But our advice is that rather than relying solely on cyber insurance, businesses should of course put in place a comprehensive cyber security strategy and continue to invest in it to protect themselves from attack as best they can in the first place.
Having certified cyber security in place not only helps to prevent cyber-attacks but reassures customers that you are working to secure your IT against this and could attract new business with the promise of having this in place. This would ideally include both preventative measures and incident response plans. It is important to invest in cyber security infrastructure such as firewalls, intrusion detection systems and incident response software. Immutable back-ups are also key to storing data and mitigating against ransomware attacks as once saved, data cannot be changed, overwritten or deleted. A company should carry out several cyber security protocols which could include reviewing email security, setting up a multi – factor authentication, protecting virtual meetings and creating a private cloud management software. In some instances, organisations working in sensitive areas will invest in the services of a SOC (security operations centre) to monitor their IT on an ongoing basis to pick up any potential attacks at a very early stage.
Hackers also rely on human error and if a company has not brought their employees up to speed on cyber security, it is only a matter of time before they regret this decision. Investing in training and education for employees on how to identify and prevent cyber-attacks is crucial. With the rise of remote and hybrid working of course providing an increased risk of data-breach, cyber security training for employees has become more important than ever.
There is no doubt about it, cyber attackers will continue proliferating the digital world. Attacks will become more frequent and more sophisticated. Whilst cyber insurance can provide some level of financial protection for businesses, it should not be viewed as a substitute for investing in robust cyber security measures including cyber security infrastructure, employee education and incident response plans. By investing in robust cyber security measures, businesses can not only reduce their risk of a cyber incident but also save money long-term by avoiding costly incidents in the first place.
Avoiding rather than just insuring is the way to beat the hackers – The Irish News
Does your business need a DR plan?
In today’s digital age, businesses heavily rely on their IT systems to carry business as usual operations. From customer data to financial records, we all store and rely on vast amounts of critical information and systems that must be protected at all costs. However, disasters and unforeseen events can and do happen, potentially causing significant disruptions to your IT infrastructure and consequently your BAU operations.
An IT DR plan is a comprehensive strategy that outlines how you will respond and recover from a wide range of IT-related disasters, including natural disasters, cyberattacks, hardware failures, or human errors. Let’s delve into the importance of having an IT DR plan:
- Minimising Downtime: Time is money, and prolonged IT system downtime can result in significant financial losses. A DR plan helps minimize downtime by providing a roadmap for recovery. By outlining the necessary steps and procedures, businesses can restore their IT systems efficiently, reducing the impact on operations and enabling a faster return to BAU.
- Protecting Business Continuity: Disruptions to IT systems can halt critical business processes, jeopardising productivity, customer service and reputation, and revenue generation. Having a plan ensures that essential operations can continue, even in the face of, and during, a disaster. By having resilient infrastructure, data redundancy, and backup internet connections, businesses can maintain continuity and provide uninterrupted services to its customers.
- Safeguarding Data: Data is the lifeblood of modern businesses, and its loss or compromise can have severe consequences. Effective DR plans includes data backup and recovery strategies that protect valuable information from permanent loss. Regular backups and secure offsite storage ensure that data can be recovered and restored, minimizing the impact of a disaster on crucial business assets.
- Enhancing Security: Cybersecurity threats continue to evolve, posing significant risks to businesses. It’s critical to ensure that any DR plan incorporates security measures and protocols that address potential vulnerabilities and mitigate the impact of cyberattacks. By proactively planning for such events, you can minimize the damage, protect sensitive data, and enhance your overall security posture.
- Meeting Regulatory Compliance: Depending on the industry, businesses may be subject to various regulatory requirements regarding data protection and business continuity. Having a DR plan ensures compliance and potentially mitigates penalties or legal repercussions that could otherwise arise.
In answer to the opening question, then YES. It absolutely does. An IT DR plan is an essential component of modern business operations. It provides a structured approach to navigate through disasters and recover from IT-related disruptions efficiently by effectively managing IT-related risks and giving your business the best chances for long-term success.
5 Best Practices for Ransomware Protection
There are three kinds of organisations in the world;
- Those who have been hacked,
- Those that are next in line or, worst of all,
- Those that don’t know they’ve already been hacked.
“Why would someone want to hack my business ?” is probably the most common mistake most businesses make. But hackers don’t discriminate – ALL businesses are targets and subject to ransomware and other cyber attacks.
When your staff navigate through the digital world they leave digital breadcrumbs. Every time they register at a website or sign up for an event, they use a username and password.
Cybercriminals are constantly, and successfully, attacking these websites and other user input points to harvest this login information which becomes the first piece in a larger, more elaborate digital jigsaw, which they piece together to create a profile and your business becomes the target.
RECOMMENDED BEST PRACTICE
The National Institute of Standards and Technology (NIST) produced its Cybersecurity framework (CSF), that sets out 5 best practice functions.
IDENTIFY: Know what you have, where you have it and the value of every single resource individually plus the value all resources combined.
PROTECT: Develop and implement appropriate safeguards to ensure critical infrastructure service delivery and proactively support your ability to limit or contain the impact of a potential cybersecurity event.
DETECT: The faster a cyber event is detected, the faster the repercussions can be mitigated. The early discovery of cybersecurity events is a critical step to a robust cyber program.
RESPOND: Develop appropriate techniques and actions to take when a cybersecurity incident has been detected. The faster and more effectively you respond to a possible detection of a cyber incident, the faster you can stop the threat in its tracks or mitigate its damage and reduce any potential financial impact.
RECOVER: Maintain appropriate plans that can be implemented to restore any impaired capabilities or disrupted services due to a cybersecurity event. Timely recovery to normal operations reduces the impact of a cybersecurity event.
Outsource and OSG Cloud both partner with the word’s leading backup and recovery technology solution providers and as NI’s only Veeam Gold Partner, Cloud and Service Provider, are best placed to support your business in ensuring you are best placed to deal with an attack and to recover after one.
We can help review your current security posture and build and implement comprehensive and robust cybersecurity program that guarantees the security and protection of your digital estate.
Don’t wait until after an event, take some pro-active steps today and make CYBER-SECURITY a priority for your business.
Get in touch for more information: info@osgroup.co.uk
#cybersecurity #security #informationsecurity #cloudsecurity
The importance of cyber resilience
At our recent Cyber Resilience event, we emphasised the famous boxing quote, “everyone has a plan until you are punched in the face,” highlighting the importance of readiness in dealing with cyber incidents.
In the same way athletes train and prepare for major sporting events, organisations need to be ready for their own “big event” in the form of a cyber incident. Achieving true cyber resilience requires a cohesive team and strategy to tackle the challenges posed by skilled adversaries, going beyond the notion of “letting IT deal with it.” This involves being prepared for the technical, organisational, and psychological aspects of incidents like ransomware attacks or data theft.
With the increasing reliance on technology, cyber-attacks have become all too common in today’s world, making it crucial for organisations to assess the impact of such incidents and determine how to contain the threat and expel the intruder from their networks. To ensure effective response capabilities, organisations must invest in resources and skills. This involves creating a comprehensive recovery plan based on best practices, employing the right personnel, and establishing fail-safe processes that can function even when key participants are unavailable. It’s important to understand that cyber resilience is not solely reliant on technological solutions – it requires a holistic approach encompassing people, processes, and technology.
However, being prepared is just the first step. To validate the effectiveness of your cyber resilience strategy, it is vital to have an intimate understanding of your business, its critical components, and how to restore them in the aftermath of an attack. To achieve this level of understanding, it is recommended to regularly and rigorously test your recovery plan. This testing helps to identify any gaps in the plan and ensure a smoother recovery process.
One highly effective method for enhancing the necessary skills and capabilities to achieve resilience is by conducting a cyber tabletop exercise. A cyber tabletop exercise is a simulated scenario that enables organisations to test and evaluate their preparedness and response capabilities in the event of a cyber incident or breach. It serves as a training tool for key stakeholders involved in managing and responding to cybersecurity incidents, including IT staff, executives, legal teams, and public relations representatives. The exercise takes place in a conference room or virtual environment and is based on realistic threats or previous incidents to provide a relevant and meaningful experience for the participating organisation.
During the exercise, participants assume specific roles and responsibilities, such as incident responders, incident commanders, legal advisors or media relations representatives. They are presented with a simulated event that unfolds gradually, and they must collaborate, make decisions, and take appropriate actions to respond to the evolving situation and adapt to new challenges that arise in a fast-moving environment.
The tabletop exercise serves several purposes:
- Testing response plans: By simulating real-world scenarios, organisations can identify gaps, weaknesses, and areas for improvement in their response strategies.
- Enhancing communication and coordination: The exercise promotes communication and coordination among different teams and stakeholders involved in incident response. It enables participants to understand each other’s roles, responsibilities, and decision-making processes, fostering better collaboration and coordination during a real incident.
- Identifying strengths and weaknesses: Through the exercise, organisations can identify their strengths, areas of expertise, vulnerabilities, and limitations in their incident response capabilities. This knowledge allows them to prioritise investments in training, external resources, and improvements to enhance their overall cybersecurity posture.
- Practicing decision-making: The exercise provides a safe environment for participants to practice making critical decisions under pressure. They can explore different response strategies, evaluate the potential consequences of their actions, and learn from their mistakes without real-world repercussions. It is better to fail during the exercise than in a real incident.
- Building familiarity with procedures: Tabletop exercises help participants become familiar with the incident response procedures, protocols, and tools that would be utilised during an actual cyber incident. This familiarity improves efficiency and effectiveness during a real incident, as responders are better prepared and more confident in their actions. It also helps external resources understand the organisation’s procedures and be better prepared to assist in an incident. This process strengthens the organisation’s cybersecurity posture and preparedness to handle real-world cyber threats.
Being aware of the latest cyber threats is a fundamental aspect of a good cyber resilience strategy. Understanding these threats enables organisations to better predict, detect, and respond to them. Conducting a tabletop exercise to test the ability to respond is critical for maintaining a high standard of cyber hygiene and informing the cybersecurity strategy.
A mature cybersecurity strategy that encompasses all aspects of threat identification, impact mitigation, and service recovery is essential. The current landscape in most organisations is characterised by technical dependency, and the rise of hybrid working models has blurred the boundaries of an organisation’s perimeter, making it harder to secure. The days of heavily investing in preventive security measures with the aim of blocking threat actors are no longer sufficient.
A paradigm shift is occurring in cybersecurity, with organisations embracing strategies such as “zero trust” that prioritise resiliency in the face of inevitable incidents. This shift necessitates partnering with strong cybersecurity providers who have the necessary technologies and knowledge to prevent or mitigate incidents while also understanding the organisation’s business context.
Ultimately, cyber resilience must be an integral aspect of a contemporary business strategy. With the increasing threats and sophistication of cyber-attacks, understanding your business’s assets, how technology supports business objectives, managing technology risk, focusing on recovery, and staying abreast of the latest threats are non-negotiable aspects.
Furthermore, it is essential to remember that a cyber resilience strategy is only as strong as its weakest link. Regular testing and investment in resources are paramount to ensure that your organisation remains strong in the face of cyber threats.
Unbreakable: Safeguard Your Data with Immutable Backups
Engaging a cloud provider to provide and ensure immutable backups is a significant strategic decision. Not all providers are the same, nor are they universally suitable for every business. There are several considerations that come in to play when evaluating the most appropriate cloud provider and its services should reflect your unique business requirements and closely align to your strategic objectives.
Consider the scalability and flexibility of the service. Your should be able to adapt, evolve and grow your business without any unnecessary disruptions or needing substantial resources to manage and migrate data.
Pay attention to security standards. You want a provider who places a high priority on data security, using strong encryption protocols, and adheres to the highest compliance standards. Remember, with immutable backups, the cloud provider essentially holds the key to your business’s existence.
Review and continually assess and challenge the provider’s reliability and disaster recovery plan. How fast and effective is the recovery process in the event of data loss? Your business continuity depends on this. The cost of downtime can quickly add up, so choosing a cloud provider that can provide a robust and reliable recovery plan is crucial.
Customer support, service level agreements (SLAs) and contractual obligations are essential. A provider with a 24/7 support system and clear, favourable and guaranteed SLAs delivers better return for your investment.
Consider the provider’s reputation. Look for demonstrable track records and customer testimonials to ensure they are trustworthy and reliable.
Remember, choosing a cloud provider isn’t just about finding a place to store your data. It’s about aligning with a partner that supports your business strategy, understands your needs, and offers the right services that’s fit and appropriate to help you grow and succeed. Carefully evaluating your own requirements and mapping them against the offerings of prospective providers will ensure that you select a partner that provides not just storage, but also long-term value and security for your business.
In essence, the cloud provider you chose for your immutable backups is a fundamental extension of your business. Much more than just a vendor; it’s a strategic partner integral to your overall success. Select wisely, because your business’s future may depend on it.
Outsource Group’s Cloud offering provides comprehensive solutions tailored to meet any requirements for frequency, retention, RPO (Recovery Point Objective), and RTO (Recovery Time Objective), along with the crucial aspect of immutable copies of data guaranteeing the ability to recover. By documenting and contractually committing to your recovery expectations, Outsource Group instils confidence and assurance. This level of business protection becomes even more critical in the current landscape of increasing ransomware and cybersecurity threats.
If you have any concerns or would like to hear more about how Outsource Group can help your business, please get in touch info@osgroup.co.uk
The End of an Era: Windows Server 2012 and 2012 R2 Reach End of Support
Microsoft has officially announced the end of support for Windows Server 2012 and 2012 R2. While it might feel a little like saying goodbye to an old friend, this necessary evolution is a crucial part of maintaining a healthy, secure, and efficient IT infrastructure.
What Does End of Support Mean?
Microsoft’s product lifecycle typically includes a period of mainstream support, followed by extended support, and then reaches the end of support. During the mainstream phase, users receive free updates, patches, and can access warranty claims. Once a product enters the extended support phase, users can still receive security updates, but other types of updates cease, and warranty claims are no longer available.
Now that Windows Server 2012 and 2012 R2 have reached the end of support, no further security updates, patches, or support assistance will be available from Microsoft. Essentially, you’re on your own.
The Risks of Running Unsupported Software
Running outdated and unsupported software exposes your infrastructure to significant risks, including:
- Security Vulnerabilities: Without ongoing security patches, your system becomes increasingly vulnerable to cyber threats. This could lead to data breaches, ransomware attacks, and other cybercrime that could severely damage your organisation’s reputation and finances.
- Non-compliance: Depending on your industry, running unsupported software might breach regulatory compliance standards, leading to hefty fines and potential legal consequences.
- Software Incompatibility: New applications and software are optimised for the latest operating systems. As a result, you might find that new software won’t run correctly on your outdated server – or won’t run at all.
- Hardware Compatibility Issues: Similarly, as hardware technology advances, older operating systems may not fully support new hardware, leading to inefficiencies or system failures.
- Increased Operational Costs: Unsupported software typically requires more maintenance and troubleshooting, resulting in higher operational costs over time.
Why You Should Upgrade or Migrate
The end of support for Windows Server 2012 and 2012 R2 signifies it’s time for businesses to upgrade or migrate to newer, supported versions such as Windows Server 2016, 2019, or take the leap into the future with Windows Server 2022. Migrating to a newer server OS provides several benefits:
- Enhanced Security: Newer versions have advanced security features that can better protect your business against evolving cyber threats.
- Improved Performance: You’ll enjoy the latest innovations in speed, efficiency, and usability with a new server operating system.
- Better Compatibility: Updated server operating systems are designed to work seamlessly with the latest software and hardware.
- Scalability and Flexibility: Advanced versions offer better options for scalability and hybrid capabilities, including seamless integration with cloud services.
- Extended Support: You’ll have peace of mind knowing that your server OS is backed by ongoing security updates, patches, and support from Microsoft.
In conclusion, while saying goodbye to Windows Server 2012 and 2012 R2, it’s a necessary step to ensure the ongoing security, efficiency, and scalability of your IT infrastructure. The risks of clinging onto unsupported software far outweigh the investment in upgrading or migrating. Embrace the future and enjoy the benefits that the latest server technology has to offer. If you have any concerns, Outsource Group can help support with inventory management, creating an upgrade plan, implementation and ongoing monitoring. Don’t be left behind and together we can help safeguard your business from potential vulnerabilities.
Choosing the Right Cloud Provider: A Strategic Decision for Business Success
In today’s digital age, harnessing the power of cloud computing is no longer just an option, but a strategic necessity for businesses of all sizes. However, with an overwhelming number of cloud providers available, making the right choice can be a daunting task.
Key factors to consider when selecting the best and most appropriate cloud infrastructure:
- Reliability and Performance: Ensure that the cloud provider has a proven track record of uptime and can deliver and guarantee the performance your business demands..
- Security and Compliance: Protecting sensitive data is paramount. Look for providers that offer strong security measures, with external validation around their technical controls and information management systems.
- Scalability and Flexibility: As your business grows, so will your cloud needs. Select a provider that offers scalability, allowing you to easily expand your resources without disruption. Flexibility is equally important, as it enables you to choose the services and features that align with your unique requirements.
- Cost-effectiveness: While cost should not be the deciding factor, it is crucial to evaluate the pricing structure and compare it against the value delivered. Consider factors like storage costs, data transfer fees, and pricing models to ensure you are getting the most bang for your buck.
- Support and Service Level Agreements (SLAs): Look for providers with a responsive support team and robust SLAs. Your cloud provider should be a reliable partner, offering timely assistance, advise and resolutions during any incidents.
Choosing the right cloud provider is a strategic decision that can shape the future of your business. By considering reliability, security, scalability, cost-effectiveness, and support, you can make an informed choice that aligns with your organisation’s unique goals and paves the way for success in the digital era. Remember, the cloud is not just a technology; it’s a catalyst for innovation and growth.
#CloudComputing #DigitalTransformation #BusinessSuccess #protection #security #recovery #backup
Breaking Free: The bold shift from hyperscalers and the emerging trend of cloud repatriation
The cloud has long been hyped as the future of computing, offering unparalleled flexibility, scalability, and cost savings to businesses of all sizes, with the hyperscalers such as Microsoft Azure, AWS and GCP being the go-to option.
Businesses have recently been reconsidering their cloud strategies, with many opting to move workloads away from the hyperscalers. This trend of cloud repatriation is driven by a variety of factors, including security concerns, rising costs, and a need for greater control over data and infrastructure.
Data Sovereignty: Concerns about where data is being stored and who has access to it. This is particularly true for businesses operating in highly regulated industries where data privacy and security are extremely important. By repatriating workloads, businesses can have complete certainty of where data is stored and who has access to it.
Costs: While hyperscalers offer a range of flexible and consumption-based pricing models, the reality is that the costs of using public clouds can quickly add up, particularly for businesses with large data sets or complex applications. Most businesses have found that the cost savings promised early on by the hyperscalers have not been realised, mainly due to the many hidden and utilisation-based costs that are difficult to understand let alone predict.
Control: Many businesses are also moving away from the hyperscalers because they want greater control over their infrastructure and data. By bringing their workloads to their own infrastructure (physical or virtual), they have complete visibility and control over their IT environment, which can be particularly important for those with complex or unique IT requirements.
Of course, cloud repatriation from hyperscalers is not without its challenges. Moving workloads from a hyperscaler can be a complex and potentially time-consuming process. Additionally, businesses may find that they are dependent on hyperscalers for certain workloads, due to geographic reach or scale, or because they have heavily developed applications using proprietary tools and services, that simply cannot be moved away.
Despite these challenges cloud repatriation is likely to continue to grow in popularity in the coming years, as businesses seek to balance the benefits of the cloud with the need for greater control, security, and cost savings. It’s important to carefully evaluate your cloud strategy and consider a multi-cloud model that best your unique business and needs.
If you have concerns on your cloud journey, where your data is stored and how transparent your cost model is, please get in touch and we can help demystify any challenges your business faces. info@osgroup.co.uk
Will Cyber Insurance solve all your security problems?
In today’s age of digital transformation, cyber security threats have become a major concern for businesses. With an alarming number of cyber-attacks and data breaches, many companies have been turning to cyber insurance to protect themselves financially in the event of an attack. However, whilst cyber insurance can help businesses get back on their feet should a cyber-attack occur, it will not solve any security concerns a business may have nor prevent a data breach. And, as always with insurance of any kind, the question is whether it will pay out at all?
The cost of cyber insurance can vary depending on the size and type of business, as well as the level of coverage. But it can be a big investment, particularly for larger companies. Before investing in cyber insurance, it is worth taking time to figure out what financial impact a cyber-attack could have on your business and how you would be covered with your insurance. Some insurance policies do not cover some common cyber-attack incidents such as money lost through business email compromise fraud or a new type of cyber-attack that does not already exist on your insurance. Insurance companies are also putting in place a very high bar – some would say impossibly high – to meet the requirements of cyber insurance. Indeed, we are seeing more and more examples of insurance companies failing to pay out in the instance of cyber-attack on the basis that the customer hadn’t met some of the (often obscure) requirements.
Cyber insurance does have a role to play. But our advice is that rather than relying solely on cyber insurance, businesses should of course put in place a comprehensive cyber security strategy and continue to invest in it to protect themselves from attack as best they can in the first place.
Having certified cyber security in place not only helps to prevent cyber-attacks but reassures customers that you are working to secure your IT against this and could attract new business with the promise of having this in place. This would ideally include both preventative measures and incident response plans. It is important to invest in cyber security infrastructure such as firewalls, intrusion detection systems and incident response software. Immutable back-ups are also key to storing data and mitigating against ransomware attacks as once saved, data cannot be changed, overwritten or deleted. A company should carry out several cyber security protocols which could include reviewing email security, setting up a multi – factor authentication, protecting virtual meetings and creating a private cloud management software. In some instances, organisations working in sensitive areas will invest in the services of a SOC (security operations centre) to monitor their IT on an ongoing basis to pick up any potential attacks at a very early stage.
Hackers also rely on human error and if a company has not brought their employees up to speed on cyber security, it is only a matter of time before they regret this decision. Investing in training and education for employees on how to identify and prevent cyber-attacks is crucial. With the rise of remote and hybrid working of course providing an increased risk of data-breach, cyber security training for employees has become more important than ever.
There is no doubt about it, cyber attackers will continue proliferating the digital world. Attacks will become more frequent and more sophisticated. Whilst cyber insurance can provide some level of financial protection for businesses, it should not be viewed as a substitute for investing in robust cyber security measures including cyber security infrastructure, employee education and incident response plans. By investing in robust cyber security measures, businesses can not only reduce their risk of a cyber incident but also save money long-term by avoiding costly incidents in the first place.
Avoiding rather than just insuring is the way to beat the hackers – The Irish News
Investing to prevent a Cybersecurity breach can save you millions
Hear from MD, Eamonn Bunting DipIoD, on his thoughts around investing to prevent a cyber security breach.
Information security and cyber security have long been seen as related but not identical subjects – information security being about protecting information in all its forms and cyber security being about protecting electronic data, with a focus on computers, networks, servers, mobile devices and so on. But such has been the rapid rate of digital transformation in recent times that information security has effectively now been absorbed into cyber security. And the instances of cyber security attacks have risen rapidly and are set to increase further in the years ahead.
By 2025, according to Gartner Inc, 30 percent of critical infrastructure organisations will experience a security breach that will result in the halting of an operations or mission-critical system. Organisations have become far more vulnerable to cyber threats because digital information and technology are now so heavily integrated into day-to-day work. The attacks themselves, which target both information and critical infrastructure, are also becoming far more sophisticated.
The fact that the European Commission recently proposed a cyber defence policy in response to Europe’s “deteriorating security environment” since Russia illegally invaded Ukraine earlier this year, shows how high up the agenda cyber security is. The Commission – citing recent cyber-attacks on energy networks, transportation infrastructure and space assets – called on member states to “significantly increase” investments in cyber security capabilities.
But cyber security can be managed, and the threat lowered. And this could potentially save your organisation millions of pounds.
Technology solutions are just a small part of the picture, and an audit is critical to an effective risk management strategy. It’s something we have significant expertise in through ANSEC AI, which became part of Outsource Group this year, and the highly specialised ANSEC team.
Our approach to cyber in the audit requires us to look at security from two different perspectives. Firstly, as a standards and regulatory driven approach where the baseline is pre-defined, and secondly as an event and risk driven approach where risks are constantly changing and the means of attack evolving.
In the aftermath of a cyber or data related incident, we very often see things that could have been identified and predicted by strong governance and audit programmes. It is therefore important to integrate cyber into any risk management and audit programme. It is also important to align organisational and technical risk.
Following a data related incident, the first question we ask is around the sensitivity of the data processed and stored on the IT applications and network used to deliver services.
According to the Information Commissioners Office (ICO), a key principle of the UK GDPR is that you process personal data securely by means of ‘appropriate technical and organisational measures’ – this is known as the ‘security principle.’
Meeting the security principle requires organisations to consider things like risk analysis, organisational policies, and physical and technical measures. They must also consider additional requirements about the security of processing activities. The ICO states that, “you can consider the state of the art and costs of implementation when deciding what measures to take – but they must be appropriate both to your circumstances and the risk your processing poses.”
The measures must also enable an organisation ‘to restore access and availability to personal data in a timely manner in the event of a physical or technical incident.’ To provide confidence in the ability to do this, ‘organisations also need to ensure that they have appropriate processes in place to test the effectiveness of the measures and undertake any required improvements.’
Identifying what is required involves understanding the link between ‘organisational and technical measures.’ Technology risks should be recorded and aligned with managing the organisational view of risk. This organisational view of control can then be independently reviewed by audit, providing an independent opinion on their operational effectiveness before an adverse event occurs.
And preventing an adverse event is key. The cost of suffering a cyber security breach can be extremely high. IBM Security research suggests that the average total cost of a data breach is almost $4million. But the effects aren’t just direct monetary costs. The impact on reputation, confidence and credibility can also be very costly. Well-managed organisations will invest to stop breaches from happening in the first place and ensure they have a recovery plan to prevent data loss.
Responding to and Securing the Future
Responding to and securing the future By Michael McCann, ANSEC IA
What is clear is that we are moving to a more integrated digital landscape. The need for cyber security is therefore more important than ever before. And it is something in which everyone must play their part, and with the rate of cyber-attacks on the rise, we all need to be prepared. Ensuring that systems are properly configured and regularly patched is absolutely critical.
For context, the Cyber Security Breaches Survey 2022 report from UK National Cyber Security Centre (NCSC) results show that in the last 12 months, 39% of UK businesses identified a cyber-attack. The survey also found that enhanced cyber security leads to higher identification of attacks, suggesting that less cyber mature organisations in this space may be underreporting.
Of the 39% of UK businesses who identified an attack, the most common threat was phishing attempts (83%). Of the 39%, around one in five (21%) identified a more sophisticated attack type such as a denial of service, malware, or ransomware attack. Despite its low prevalence, organisations cited ransomware as a major threat, with 56% of businesses having a policy not to pay ransoms.
At ANSEC, cyber response is what we do, and we see an ever-increasing sophistication in cyber threats. Organisations must work diligently to stay ahead. As a business, understanding the risk to your organisation is the first step in your defence. Many companies are investing in the latest technologies and solutions in order to improve their own automation. This includes artificial intelligence and machine learning, to better detect, prevent and respond to threats. Solutions such as Extended Detection and Response (XDR) and Security Orchestration Automation and Response (SOAR) are being used to analyse patterns in digital activity and flag potential threats. These automated processes lead to faster response times which have proven invaluable in halting a cyber-attack before it escalates.
Some larger organisations are investigating the use of tools such as ‘honeypots’ – a virtual trap to lure attackers which means that businesses can study techniques and indicators of compromise to improve security policies and processes.
So, what can SMEs do?
Understanding and testing plans across all areas of business – not just those controlled by IT -continues to be extremely important. In addressing the possible repercussions of security incidents, it is vital to ensure that all business stakeholders understand how to:
- invoke the plan;
- utilise the platform on which it will operate;
- have a clear understanding of the steps needed to support mitigation.
Simulating common breaches increases corporate cognitive ‘muscle memory’ and sharpens the skills needed to execute response playbooks and runbooks, should a breach occur. Learnings from such exercises help to improve the security and the posture of any organisation, large or small.
Many cyber-attacks are successfully launched due to user error. Educating users and leadership boards provides a key foundation in preventing attacks from being able to progress through cyber security best practice, such as:
- using secure passwords;
- multi factor authentication;
- avoiding suspicious links or attachments.
By investing in the right technologies, anticipating incidents, educating users, and better leveraging existing security assets to defend against attacks, organisations can ensure that they remain secure in the face of the ever-evolving cyber threat landscape.
Is Cyber Insurance worth the paper it’s written?
A lot of companies are looking at Cyber Insurance, however, the article from ‘Zurich Insurance CEO: Cyber Attacks will be ‘Unisurable’ indicates there is a thought that a cyberattack may be become uninsurable, why is that? Hear from Kevin Lyons, 3rd Line Engineer, at Outsource Group talk about how to mitigate against this and limit your attack surface.
Besides potential loss of data there are days of lost or disrupted productivity investigating, restoring and rebuilding the system.
I have worked with some great people in the cybersecurity field and concluded no system can ever be completely protected; all you can do is make your attack surface as small as possible and put up as many defences as possible and hope that the potential attackers move on or a breach is limited. How do you do this?
1. Limit where company data can be accessed – if a user has three devices it is a bigger attack surface than a user having one device.
2. Think seriously about BYOD – are users accessing data with devices that have at least equivalent security to your company devices?
3. Are all systems as up to date as they can be – how do you patch Microsoft products, well generally through Windows update but what about other applications on your systems?
4. Are you running out of date systems because of out of date applications? – a company’s key system maybe does not run on the latest version of Windows so the older version of Windows is sometimes at the heart of their network potentially exposing every other connected system.
5. Do you have proper segregation in place, do external people come in and connect to your corporate Wi-Fi? – there is no feeling what their device has on it and how it could potentially interact with your systems.
6. Do you setup and review security groups for folders and applications? – if a user does not need access to a share file share/application then them having it increases the attack surface.
7. Last but not least are your users aware of the threat out there? – users sometimes think that IT is there to stop them doing something because they don’t like it; the problem is sometimes the user’s ‘solution’ actually creates a bigger security hole as they don’t understand why access is being restricted. Talk to the users and let them know what you are up against.
If there are any questions then please ask us Outsource Group or ANSEC IA LTD
#cybersecurity #segregation #cyberattack #updates #domain #userexperience #awarenesstraining #byod
The heightened case for cloud in a high energy cost world
Much research has been conducted into the energy efficiency of cloud computing. Most of it was done a few years ago. But it’s even more relevant now, as energy costs for businesses have spiralled to levels that even the gloomiest wouldn’t have predicted.
Microsoft’s efforts, conducted in conjunction with WSP Global Inc, concluded that cloud computing is 93 percent more energy-efficient and has 98 percent lower greenhouse gas emissions than on-premises data centres.
AWS (one of the other ‘Big 3’ public cloud providers) used its billions to deduce through research that businesses can reduce energy use by nearly 80 percent when they run their applications on the cloud instead of operating their own data centres.
In today’s price terms, that’s a very significant monetary saving for a business. Some estimates suggest that businesses in NI are paying vastly more for their energy now than they were in 2020.
The AWS report found that compared to the computing resources of the average European company, cloud servers are roughly three times more energy efficient and that migrating compute workloads to the cloud across Europe could decrease greenhouse gas emissions equal to the footprint of millions of households.
Collaborative research by Berkeley Lab and Northwestern University and funded by Google (the other part of the big tripartite) found that cloud computing can cut energy consumption by 87 percent. The report noted that the saved energy in the US alone could power Los Angeles for a year. The survey affirmed that organisations could save between 60 percent and 85 percent in energy costs when they shift to cloud-based services.
As much as we compete with AWS, Microsoft Azure and Google through our OSG Cloud platform, we agree with their findings about the energy efficiency of cloud.
That’s because modern, purpose-built data centres are designed to run as efficiently as possible. Commercial cloud services can operate more economically than smaller on-premises operations, with large-scale dynamic provisioning and multitenant architecture.
Cloud data centres are also efficient because cloud providers focus on sustainability across their entire operation. In contrast, most businesses don’t prioritise their data centre infrastructure sustainability, because digital infrastructure is not their core business.
Cloud providers focus on efficiency as a best practice. They operate servers at much higher utilisation rates and design facilities to use less energy and water.
This helps reduce overall energy consumption and associated costs, but equally importantly, delivers good corporate responsibility by continuously focusing on improvement to further help reduce carbon footprints and ultimately achieve sustainability. Demand for consolidated electricity by commercial cloud providers creates the potential for large-scale purchases of green energy that would otherwise be unfeasible.
OSG Cloud for instance uses 100 percent renewable energy and by providing a multi-tenanted cloud platform to its customers further maximises these efficiencies, resulting in an overall reduction in aggregate energy consumption when compared to customers running the equivalent server footprint on-premise.
We’ve been encouraging customers to consider a move to the cloud for years. Now more than ever, with energy costs so high, businesses really need look into whether doing so could save them large sums of money as well as improve their IT infrastructure.
Have you thought about your applications and third party access and access rights?
In the Blog post below, Network Engineer Kevin Lyons talks about the threat of 3rd party access rights over applications.
Over the years, I have come across third parties which will insist on Domain Admin rights, just to install a piece of software on a server and a few workstations. I have worked with a company where the third party would not give a date for install without granting Domain Admin rights. The reasons given where not justified – such as ‘because it prevents issues during the install’ and ‘because that is required’. As an Network Engineer, I have dealt with a third party company who wanted to add users to the Domain Admin groups to prevent issues and it is the access needed to run in order to execute on the elevation. In this case and usually if planned properly, the correct access to a key folder was sufficient.
What can be insisted on are generally Domain Admin accounts which also run services and have non-expiring weak passwords.
Whenever a company comes on board with Outsource Group, one of the first things we do is check who are members of the Admin groups in Active Directory; the record so far was 75 accounts (a combination third party accounts and users) to run a certain piece of software, the reason given was ‘because it is needed when there is an update to the software’. On investigation the users required ‘modify’ access to a sub-folder of the program files directory.
The concerning part is users had no idea what power they wield as one mis-click could authorise an encryption of an entire domain. When thinking about the insider threat, intentional or not we have to consider what permissions our application support companies request for both themselves and the users of their system and why.
If there are any questions then please ask us at Outsource Group
#cybersecurity #microsoft #credentials #adminrights #insiderthreat #permissions #security #mssp #whensecuritymatters
The Hallmarks of a Disruptor – Better, Faster, and More Affordable
OSG Cloud is a relatively new entrant to the market. With our first 12 months of operations and trading now under our belt, we’ve onboarded 50 new customers, revenues in excess of £1M+ (the lion’s share of this once went to Microsoft’s Azure!), and achieved a 100% success rate with every customer that put the platform to the test through trial workloads, now committing fully to OSG.
How?
Being Better, Faster, and More Affordable.
Better: We’ve invested in the best technologies and partnered with the best vendors available enabling us to stand over all elements of the service; not just the underpinning infrastructure, but all the way up the service delivery and management stack. All backed by robust SLAs and KPIs for application availability, security, management and governance.
Faster: Application and IT performance is key to improving the end users’ experience, business efficiencies and results. OSG Cloud is designed exclusively for Enterprise IT workloads, focused on one class of service that guarantees to outperform any On-premise, Public, or Private Cloud infrastructure.
More Affordable: On average, our service is 15% more cost effective when compared spec-for-spec against the big Hyperscalers and we can prove it. More importantly, we also offer complete budget certainly with predictable and transparent pricing. No more ‘bill shock’ or being penalised for trying to improve your users experience, applications and business performance.
If you’re currently, or considering, running your enterprise IT on cloud infrastructure, then please give us a shout at info@osgroup.co.uk. We can help you understand the true cost of Public Cloud, as well architect the most appropriate cloud solution and IT operating model.
What is MFA, and why is it critical to keeping your organisation secure?
We know that just using passwords is a security threat and we should all use 2FA. Or MFA, as it is now known.
But what is MFA and why is it so important?
MFA is comprised of 3 areas.
- Something you know: This could be a PIN or a password
- Something you have: This could be an Authenticator App.
- Something you are: This could be a fingerprint or face scan.
If you have a combination of two or more of the above, it is classed as MFA. If you have two of one area, for example a password and a PIN, then it is not classed as MFA.
But did you know not all MFA systems are equal? Older MFA systems are being ‘defeated’ by hackers.
Text message systems are no longer advised as ‘secure’, as it has been demonstrated that SMS text messages are often the weakest link in two-step logins. It is possible for hackers to sometimes hijack the SMS messages meant to keep you safe. Or even sim-swapping which means your authorisation code text message may arrive at a different or duplicate phone.
Whenever possible, it’s worth taking a minute to switch to a better system such as an Authenticator App.
Thinking of systems, no matter how strong they are, the weakest link is generally the user. Recent studies show that if a particular account is attacked multiple times and a user gets multiple prompts on their Authenticator, they are likely to hit ‘Approve’ at some point to stop the annoyance.
Before implementing MFA into an organisation, users on all levels should be fully engaged and educated on their responsibilities. They should know that if they are getting multiple prompts or unexpected prompts then they should be investigated.
Get in touch with our team at Outsource Group to discuss MFA and how we can implement it to keep your organisation secure – info@osgroup.co.uk
Migrate, Manage, Monitor
Not many businesses have the luxury of dedicated inhouse cloud specialists to configure, manage and monitor their public cloud environments, to allow them to extract maximum performance and cost efficiencies from their current cloud provider.
Our service is designed to not only deliver market beating performance, but to provide a high standard of manged services to those businesses that do not have the time, resources, or funds to make the levels of commitment required to fully exploit cloud technologies.
We take ownership and responsibility for migrating, monitoring and managing your applications in the cloud. To date, every business that has trialled a free workload has made a business decision to partner with us and embrace a cloud operating model. If requirements dictate specific types of cloud services, tools, reach etc, we can leverage tier 1 public cloud infrastructures and services, integrating seamlessly to deliver a truly hybrid cloud solution; allowing business to cherry pick the best bits of all the available options.
We remove price uncertainty and offer guaranteed fixed pricing, enabling businesses to understand, plan and control budgets better.
Why not get in touch to see how we can help your business?
#business #cloud
Customer loyalty should be rewarded, not punished
By now, most of us will have digested Microsoft’s recent licensing / price changes. As difficult as they can be to swallow, the fact remains that there really is limited choice, other than to simply choke it down.
Of course, it does trigger the need to review your license base and ensure you are licensing your users, devices, and services in the most cost-effective way. Unfortunately, the outcome is always the same, and the vendor related spend keeps going up.
As a cloud service provider, we’re often stuck in the middle and typically end up being the bearer of bad news when vendors unilaterally decide to impose these charges.
However, we fully understand the bad taste that this can leave. So instead of punishing customer loyalty, we want to reward it by not passing price increases through to our existing customers. The rate card you have today for your cloud services, will always be your rate card. So anytime a vendor pushes out an increase to its license costs, we will absorb those costs; essentially passing that on as a de facto discount or reward for your loyalty.
If your cloud bills are considerably more today than what you had originally planned and budgeted for, then get in touch. We can help get your cloud costs under control and provide a guaranteed fixed price, whilst delivering better performance, for your cloud server estate.
Ransomware Protection – 5 Best Practices
There are three kinds of organisations in the world;
- Those who have been hacked,
- Those that are next in line or, worst of all,
- Those that don’t know they’ve already been hacked.
“Why would someone want to hack my business ?” is probably the most common mistake most businesses make. But hackers don’t discriminate – ALL businesses are targets and subject to ransomware and other cyber attacks.
When your staff navigate through the digital world they leave digital breadcrumbs. Every time they register at a website or sign up for an event, they use a username and password.
Cybercriminals are constantly, and successfully, attacking these websites and other user input points to harvest this login information which becomes the first piece in a larger, more elaborate digital jigsaw, which they piece together to create a profile and your business becomes the target.
RECOMMENDED BEST PRACTICE
The National Institute of Standards and Technology (NIST) produced its Cybersecurity framework (CSF), that sets out 5 best practice functions.
IDENTIFY: Know what you have, where you have it and the value of every single resource individually plus the value all resources combined.
PROTECT: Develop and implement appropriate safeguards to ensure critical infrastructure service delivery and proactively support your ability to limit or contain the impact of a potential cybersecurity event.
DETECT: The faster a cyber event is detected, the faster the repercussions can be mitigated. The early discovery of cybersecurity events is a critical step to a robust cyber program.
RESPOND: Develop appropriate techniques and actions to take when a cybersecurity incident has been detected. The faster and more effectively you respond to a possible detection of a cyber incident, the faster you can stop the threat in its tracks or mitigate its damage and reduce any potential financial impact.
RECOVER: Maintain appropriate plans that can be implemented to restore any impaired capabilities or disrupted services due to a cybersecurity event. Timely recovery to normal operations reduces the impact of a cybersecurity event.
Outsource and OSG Cloud both partner with the word’s leading backup and recovery technology solution providers and as NI’s only Veeam Gold Partner, Cloud and Service Provider, are best placed to support your business in ensuring you are best placed to deal with an attack and to recover after one.
We can help review your current security posture and build and implement comprehensive and robust cybersecurity program that guarantees the security and protection of your digital estate.
Don’t wait until after an event, take some pro-active steps today and make CYBER-SECURITY a priority for your business.
Get in touch for more information: info@osgroup.co.uk
#cybersecurity #security #informationsecurity #cloudsecurity

The Unrelenting Rise of PHISHING !
Fishing, already one of the world’s top participation sports, has again grown in popularity since the onset of Covid but unfortunately pales into insignificance compared to the unprecedented rise of Phishing Attacks on businesses during the same period.
Recent UK Government statistics tell us 65% of businesses have experienced a cyber security breach or attack in the last 12 months, with Phishing Attacks the stand out weapon of choice for criminals to steal data/information or extort money.
What is Phishing ?
Phishing is where attackers use multiple attack routes (email, mobile, social media, telephones, text message etc) to trick users into taking an action eg click a link for example, which provides them with the opportunity to steal, corrupt or hold a company to randsom.
Steps to Mitigate and Minimise ?
Following some basic steps will give your business some greater protection, including;
1. TRAINING – Implement staff training and security awareness programmes. In-House or trusted IT partners can provide staff ongoing training included regular unannounced simulated phishing exercises.
2. ANTI-VIRUS SOFTWARE – Use reputable and up to date Anti-Virus software
3. FIREWALLS – Use Desktop and Network Firewalls – have professionally configured and managed.
4. BROWSER – Keep it up to date with all new security patches to ensure newly identified loopholes are closed.
5. POP UPS – Remain vigilant of ALL pop-ups, even if they look legitimate.
6. SITE SECURITY – verify the security of a site before you use it.
7. PERSONAL INFORMATION – where possible share as little personal information on the internet you can.
8. PASSWORDS – implement and follow password security guidelines (complex / three random words)
9. MFA – a basic security requirement (no caveats)
10. THINK BEFORE YOU CLICK – “act in haste repent at leisure” – any time you feel under pressure to act or respond quickly should be considered a red flag to take a breath.
Finally, where people are involved we will always be subject to human error and so when all else fails and in anticipation of a successful breach – HAVE A PLAN, PREPARED IN ADVANCE, so you can take the right actions, in a timely manner, to minimise losses and disruption.
To find out more about ways you can assess your vulnerabilities and improve your cyber security readiness get in touch.
Multi Factor Authentication – is BASELINE security.
Multifactor Authentication (MFA) is a BASELINE security requirement for your Business. It is no longer considered an option if you value the security of your business.
To underpin the point, President Biden has recently signed an Executive Order making MFA a non-negotiable requirement for all US government agencies, with immediate effect
Outsource recommend businesses continue to maintain a robust security stance using group policies to ensure staff avoid the use of simple, non-complex passwords. The National Cyber Security Centre’s current recommendation for a strong password is to use three random memorable words, “ RedPantsTrees4! ”.Longer and complex alpha numeric passwords also remain acceptable.
However even complex passwords remain vulnerable to exploit. The IT security community believe the incorporation of the additional layer of MFA security is a must to help maintain the integrity and safety of your business networks. It simply provides an additional layer of security, a safety net, when for whatever reason a password has been compromised. It just requires a user to present two pieces of evidence as verification before they can gain access.
MFA is not new and you will already use it in your own personal life. From the moment you swipe your bank card at the ATM and need to verify by a PIN number to your online purchase where you are then required to enter a numeric code sent to your phone/e-mail address.
In order to verify users MFA offers a range of options falling into one of the following three primary categories:
– Something you know (like a password or PIN)
– Something you have (like a smart card/one-off code/clicking – – Approve on an authenticator)
– Something you are (like your fingerprint/face ID).
As technology evolves and security threats continue to increase expect to see the increasing use of more specific security measures such as Adaptive MFA. This will further increase your security stance by tailoring verification to user roles, security levels, approved permissions, location, log in behaviour etc. These variables when chosen will all feed into each individual users specific log in requirements. However for today the minimum requirement as confirmed by all reputable Security experts must be the deployment of MFA.
If the importance of MFA has not been stressed enough by your existing IT provider or your internal IT team you need to ask why and if required seek advice from another reputable Security adviser.
For the effective protection of your Network and your Users it is time to ask yourself “why do we not already have MFA in our business ?”
Get in touch to discuss how the Outsource Group can support your Cyber Security and IT needs, for today and tomorrow.
Ransomware – 5 Best Practices
There are three kinds of organisations in the world — those who have been hacked, those that are next in line or, worst of all, those that don’t know they’ve already been hacked.
Thinking that you and your business won’t be a target, or that you don’t have any valuable or interesting data, is a false sense of security and the most common mistake most people make.
As you navigate through the digital world, you leave digital traces behind like digital breadcrumbs. Every time you register at a website, or even simply sign up for an event, you use a username and password. The username is usually your email address and the password is, for 60 % of people, a re-used password.
Cybercriminals are constantly, and successfully, attacking these websites to harvest login information like email addresses, login names, domain names and any other information they can retrieve. This is just the first piece in a larger, more elaborate digital jigsaw. The data they retrieve will be placed in cloud caches, analysed and enriched with other data sources like a social media post, LinkedIn profiles and multiple other telling pieces of information that is readily available.
As soon as cybercriminals establish relationships between these digital jigsaw pieces, they create a profile and you become a target. Armed with this digital profile, they have the keys and further opportunities to gain access to newer, larger and more sensitive data sources. Every piece of additional information they gather, brings them many strides closer to successfully hacking you personally, and worse still, your extremely valuable corporate IT systems.
The National Institute of Standards and Technology (NIST) produced its Cybersecurity framework (CSF), that sets out 5 best practice functions that are widely considered to be the default standard for building a robust cybersecurity program. They are applicable to organisations of all sizes, and all industries, whether you’re just getting started in establishing a cybersecurity program, or if you’re already running a mature program.
- Identify: Know what you have, where you have it and the value is of every single resource individually plus the value all resources combined.
- Protect: Develop and implement appropriate safeguards to ensure critical infrastructure service delivery and proactively support your ability to limit or contain the impact of a potential cybersecurity event.
- Detect: The faster a cyber event is detected, the faster the repercussions can be mitigated. The early discovery of cybersecurity events is a critical step to a robust cyber program
- Respond: Develop appropriate techniques and actions to take when a cybersecurity incident has been detected. The faster and more effectively you respond to a possible detection of a cyber incident, the faster you can stop the threat in its tracks or mitigate its damage and reduce any potential financial impact.
- Recover: Maintain appropriate plans that can be implemented to restore any impaired capabilities or disrupted services due to a cybersecurity event. Timely recovery to normal operations reduces the impact of a cybersecurity event.
OSG partners with industry leading backup and recovery technology solution providers. We can help review your current security posture and build and implement comprehensive and robust cybersecurity program that guarantees the security and protection of your digital estate.
Importantly, we provide you with the absolute confidence, backed by contractual commitments and SLAs, that your business can recover from any incident within an acceptable, defined and predictable timeframe.
Don’t wait until after an event, take some pro-active steps today and make security a priority for your business.

Record Breaking Performance
It’s that season again where sport is dominating the headlines and screens are filled with athletes competing and pushing themselves to achieve their absolute best on the world stage of the Olympics. Everyone is striving to attain the top performing gold medal and make their home country proud
Like Paul O’Donovan and Fintan McCarthy, who won Ireland’s first gold medal of the Tokyo Olympics on Thursday with a stunning victory in the lightweight men’s double sculls. Hours on the water and years of training paid off.
In a humorous interview with the BBC, asked how being an Olympic gold medal-winning athlete sounded, O’Donovan said: “It’s alright, yeah. You can’t complain about it really. I wouldn’t go around introducing myself like that though.”
He seems fully aware and not at all bothered that the Olympic coverage will fade over time and will likely be happy to get back on the water and “do what we always do, the best we can.”
Some similarities could be drawn to the initial hype around Public Cloud. When first launched over a decade ago it promised infinite scale, global reach, on-demand flexibility, rapid deployment, super low unit cost and consumption based ‘only pay for what you use’ billing.
Public Cloud has delivered on all these areas. In most cases exceeding expectations. The exception to this is costs – the reality of the super low unit cost and consumption-based billing model, is increased costs. Not the savings everyone expected.
There is no doubt that if time is spent using cost calculators available (note: these are sales and marketing tools), the numbers always look favourable. However, the unit-based costs are allocated to absolutely everything – including things that happen ‘under the hood’ on the platform that most people don’t understand, let alone know how to translate their own requirements and use cases to.
This is in absolutely no way a failing or misrepresentation by Public Cloud providers. They’ve been upfront and honest with their transparent pricing and low unit costs. It’s simple misunderstanding, people getting carried away with all the hype, that has led most businesses to expect to achieve considerable cost savings, by moving to Public Cloud.
There will always be examples of companies that have achieved reduced costs. However, organisations that are heavy users of IT or applications, or just have heavy applications, often, will have realised considerably higher costs post move.
In addition to increased costs, another unexpected or undesired realisation is lack of certainty or predictability around monthly costs. Cloud infrastructure and resources are not consumed in a uniform or consistent way, leading to variables that are difficult to predict, manage, and in some cases impossible to control, leaving budget holders with an unenviable task.
Public Cloud does, and will, always have its place.
However, companies that have embraced these platforms should begin to review their longer-term strategies; and consider a multi-cloud operating model which is becoming ever more prevalent. Which involves moving those applications that don’t necessarily need global reach or hyper scale whilst still having access to all the other goodness that Cloud offers. Including typically high levels of performance, that can be delivered close to their end users
No matter where you are on your journey, it’s important to review and assess regularly to make sure you are embracing the technologies and platforms that allows you to evolve and adapt, and not be locked in to any one vendor or platform.
Not all clouds are created equally.
No one size fits all. It will take a hybrid and multi cloud approach and operating model to best fit all your requirements (known and unknown). That may include public cloud, but most likely will incorporate specialist private and hybrid cloud platforms managed by trusted partners and delivered closer to home, and importantly closer to your end users.
OSG provides an enterprise grade private and hybrid cloud platform, with guaranteed performance, recoverability, with predictable commercials.
For us it will never be about the hype but doing the best we can with the technology available to ensure your business can always access gold medal standard cloud services and solutions.
Get in touch to discuss how we can help your business leverage cloud.
Failing to Plan is Planning to Fail.
Having a disaster recovery plan for your business is prudent, it’s a de facto insurance policy for your business.
Getting to that point of having a policy in place that is fit for purpose and appropriate for your business (and allows you to sleep easy at night) can be a journey in itself. It may seem daunting from the outset, but choosing the right partner to help you navigate your way through the process is essential and can help underwrite the entire service when you come to rely on it the most.
The 5 essential things to identify are:
- Scope – what should be included in your recovery plan
- Review your users, systems and data, and identify what you rely and depend on the most and evaluate the impact should they become unavailable either temporarily or permanently.
- Recovery Time Objective (RTO)
- Once you’ve identified all the relevant components that need to be considered as part of any recovery activities, you should then prioritise each – those that need to be recovered first, second and so on. This will inform the recovery plan, and defines the recovery time objectives (RTO) for your IT services and users.
- Recovery Point Objective (RPO)
- Next you need to establish what your tolerance, if any, is to partial and / or complete data loss. This will determine your recovery point objectives (RPO) – the point in time that if you recovered to, you could comfortably continue in an almost business as usual way, without any material impact P&L, productivity, services, customers, and suppliers.
- What are the scenarios that might trigger a recovery event?
- Completing some scenario and ‘what if’ planning will help shape the plan, as you will quickly understand the ramifications of different types of events, as well as the practicalities of what the recovery would or needs to look like. This, along with your scope, RTO and RPO will underpin your DR plan and identify any extra resources or services that need to be in place to facilitate it.
- Pick the right partner and technology.
- Most importantly you need to engage a partner that you can trust, and you know will be by your side through out what could be one of the darkest and most stressful times your business has faced. It’s no good picking a vendor to install a solution and then walk away. Over time, systems, people, priorities will change, so it’s important that the recovery solution is regularly reviewed for appropriateness, as well as fully tested and verified against the plan. Your chosen partner needs to be contractually retained to fully assist in a recovery event, so that they are responsible and accountable for the solution.
There are different technologies, services, approaches and methods for recovery, and it’s likely that the right plan for you will have some combination of these.
If, at a minimum, you nail 1 to 5 then you can take comfort that when you come to rely on your DR plan the most, your expectations will be fully met with no surprises when you execute your plan.
We provide a full suite of recovery options, ranging from
- Back-up as a Service,
- Disaster Recovery as a Service
- And, recently launched ‘World First’, Failover as a Service.
If you don’t yet have a suitable DR or recovery plan, or are lacking complete confidence with what you have, then get in touch. Let our expert team design the best solution for you, that we will 100% stand over and underwrite.

On The Road To Recovery
Recovery has been talked about a lot over the last few months, as we look forward to the new post-pandemic world. Without doubt everything has changed and our way of living and working will be different. Some good, some bad.
Perhaps now we all understand better how important recovery is across every aspect of our lives, businesses, and worlds. It’s a common thread that exists across almost everything: economies, environment, sport, health, relationships, a good night out; the list is endless!
The principles of recovery are common:
- It’s about getting back on your feet;
- And recovering to at least the position you were before, or a better one.
Recovery can be approached in two ways: reactively or proactively. Most of us take a reactive approach, we roll with the punches, re-evaluate, and cut our cloth accordingly. That’s absolutely fine for the majority of things that we face personally.
However, for the really important things that have the potential to impact populations, industries, our businesses and our livelihoods; we must be pro-active. That means, everyone needs to plan for the worse case scenario, and be sure those plans can stand up to the test when they are needed the most.
Before the event, it’s very difficult to conceive how real the risk of the worst happening actually is.
- Pre 9/11 no one could have imagined those horrific events unfolding;
- Pre 2008 no one could have predicted just how quick and deep the financial impact would hit;
- Pre 2020 and Covid, enough said…
With the benefit of hindsight and our newfound experiences of these events; looking back it was almost, inevitable. Simply a matter of time.
It’s important that we learn from history, and make sure that we’re always prepared for the worst. There is no need to try and foresee every possible eventuality or categorise every tiny conceivable risk that might trigger an event. However , we do need to think about the impact and the potential “what ifs” of an event itself.
In the context of IT and recovery, it should not be about all the things that could cause an availability issue, a security breach, or corruption (or even worse crypto locking) of data. The cause is irrelevant (in the context of recovery – prevention and mitigation, well that’s one for another day). Instead, the focus should be on what the impact of the event is to our business, and make sure that we have a plan, tried, tested and continually verified; that can be executed, when needed, that will enable the business to get back as quickly as possible to at least the same position it was previously.
The ugly truth of recent months is that the worst does and will happen.
Only you can decide how impactful or disastrous that might be to your business, and if it deserves a reactive or proactive response.
Want to know more about what you can do right now to put your business in the best position?
Get in touch with one of our team to find out more. Take action today.
Cyber Security Is Essential in our Digitally Connected World.
According to Forbes “The year 2020 broke all records when it came to data lost in breaches and sheer numbers of cyber-attacks on companies, government, and individuals.”
Ignoring the problem of cyber crime only increases the threat risk, potential reputational damage and financial loss to your business. Use of online services, smart devices and digital transformation across every industry means that cyber security is not just an issue for enterprise business’, but for SME’s, smaller business’ and individuals alike.
If you spend anytime online you should consider how cyber-safe your devices, network and personal data are.
At Outsource we believe in leading by example. As we advise, support and implement security controls for customers the least we can do is make the effort to prove our own internal security protocols are strong enough to pass rigorous independent audits and challenges on an annual basis.
We have been independently assessed and been awarded certification to confirm that we comply with the requirements of the Cyber Essentials Plus Standard.
Theses audits includes external/internal penetration testing and comprehensive reviews of areas including;
– Boundary Firewalls & Internet Gateways
– Secure Configuration
– Patch Management
– Access Gateway (User accounts)
– Malware Protection
No business can ever be 100% secure against external threats, but accreditations such as CE and definitely CE Plus will mitigate your exposure significantly.
What is Cyber Essentials?
In order to adopt good practices in information security, the UK government Department for Business, Innovation and Skills released a government-endorsed scheme called Cyber Essentials in 2014.
The scheme was introduced to ensure the protection of data, and to help companies understand how data can be used, secured, or compromised. The scheme ensures that data is protected from common cyber threats online. Organisations can gain one of two Cyber Essentials badges, and it’s backed by the Federation of Small Businesses, the CBI, and many insurance companies who offer incentives to businesses.
The Cyber Essentials certification is required for any suppliers to the UK government who handle any sensitive and personal information, and any companies bidding for government contracts must achieve this certification.
Cyber Essentials Plus is the highest credential offered by the NCSC.
Cyber security threats are constantly evolving and what works today won’t necessarily work tomorrow, which is why it’s so important to continually review and refine strategies to keep your business safe and protected.
At Outsource we are committed to continually developing our processes and striving to deliver the highest possible standards that everyone can benefit from.
To find out more about ways you can assess and improve your business readiness to security vulnerabilities get in touch.
The National Cyber Security Centre (NCSC) website also has further info on Cyber Essentials Plus Certification as well as advice and steps you can take to protect you and your business from cyber crime.

First Dell Cloud Service Provider in Northern Ireland.
OSG Cloud are proud to be recognised as the first, and only, Dell Cloud Provider in Northern Ireland
For over 20 years Outsource have enabled businesses across the UK and Ireland to solve tomorrow’s problems today. We take care of our customers’ technology needs and make life better so they can focus on what is really important, their people, business and customers.
Our team of experts have been collaborating with the team at Dell Technologies to create, design and deliver world class cloud services to enable us to rapidly deploy scalable infrastructure for our customers. OSG Cloud delivers scalable, secure, high performing solutions to maximise the agility needed by business to drive success and enable growth in our rapidly changing digital world.
The hybrid cloud infrastructure on Dell’s VxRail and Unity platforms, powered by Intel and VMWare provides us with exactly what we need to deliver guaranteed performance, security and availability to our customers.
OSG Cloud removes the barriers and complexities of cloud enablement to allow businesses to choose an IT delivery model that fully meets their exact needs.
Check out our video gallery to hear more from Jason Ward, VP Dell Technologies, Terry Moore and Brian McCrory on what they think about this achievement.
Safe, Secure, Compliant Communications
Businesses are justifiably nervous, the security threat to every business is growing, the risk is real. Every organisation recognises the consequences of inadequate security, compliance and reliability in communications systems.
- Data breaches make headlines and affect reputations.
- Privacy violations put companies at legal risks.
- Downtime results in lost revenue.
- Recovering from hacking or fraud is costly and a distraction from where management want to focus attention.
We Take Security Seriously.
We talk plainly about it because we can provide secure, compliant and reliable services.
Talk to us to find out more about how we can deliver secure voice, cloud communication solutions for your business with our telecoms partner 8×8.
Achieve your security and compliance goals.
From physical security to data at rest or in motion, 8×8 is protecting your business using the highest levels of security and compliance policies and procedures – verified by 3rd party security and compliance certifications including:
- HIPAA
- NIST/FISMA
- Privacy Shield Framework
- ISO 27001 and 9001
- PCI
- Skyhigh CloudTrust and the Cloud Security Alliance Star Compliance
- GDPR
- U.K. Government G-Cloud
- Cyber Essentials Plus
8×8 offer one platform for voice, video and chat. Services are developed with privacy and security in mind, they own their technology stack allowing them to prioritise our customers’ PCI compliance needs. Infrastructure is developed to keep up with evolving standards. When changes are needed, everything can be quickly adapted and transparently communicated with customers without waiting on third party technology providers to modify their components.
Ready to Learn More?
Contact our Telecoms Solutions Expert to learn more about how together with 8×8 we can help enhance security and compliance for your business through one system of engagement that integrates voice, video, chat and contact centre capabilities.
Poor Connectivity Can Cripple Productivity.
Poor Connectivity can cripple business productivity. Not surprisingly then, many businesses are looking at leased line connectivity as a solution and an alternative to broadband. Effectively, a leased line is a dedicated Ethernet connection direct to the Internet.
How much does a leased line cost?
Frustratingly, there isn’t a simple, easy answer. The reason? Leased line costs depend on a number of business-specific variables:
Location. A leased line involves creating a direct fibre optic connection between your business and the nearest ‘Point of Presence’, this is usually an exchange or carrier datacentre, which can be up to 35km away. The longer that connection, the greater the cost.
Bandwidth. Basically, the faster the connection, and the greater the amount of traffic that it has to carry, then the higher the cost. A business simply wanting a fast and reliable connection for 20 people, say, is therefore going to pay a lot less than a 200-employee business with heavy cloud-computing and enterprise systems workloads.
Contract length. From a leased line provider’s point of view, there are a lot of fixed costs involved in setting up a leased line connection. The longer you’re prepared to be a customer, the lower your monthly payment.
Required levels of customer service, latency, resilience, and uptime provisions. As always, you tend to get what you pay for. And as with consumer broadband offerings, cut-price business connectivity can often mean compromises on performance and service.
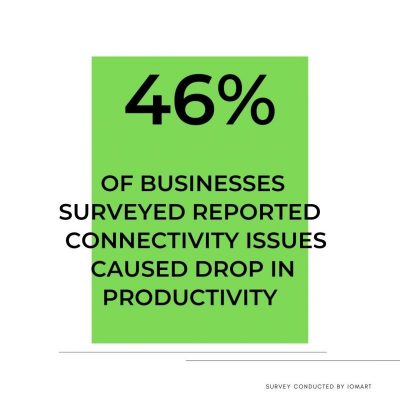
Make Informed Decisions
It is important to really understand what your bandwidth requirement is going to be, as not every leased line provider will offer an ability to flex your leased line’s bandwidth as your needs evolve. Bandwidth calculations aren’t easy, technology evolves at a rapid pace which may increase your business demands.
Different leased line providers will have different leased line infrastructure in place to serve businesses’ differing location and bandwidth situations. It really does pay to shop around—especially if your business is located a little off the beaten track: cities and busy business parks are better served than more rural locations.
Getting The Best Solution
It is a complex marketplace, thanks to those differing leased line infrastructure footprints, and differing service and uptime provisions. To ensure you get the best prices and the most appropriate leased line capability, we obtain a ‘whole of market’ comparison with our connectivity partner Aspire, who work with all leased line providers including Virgin Media, Sky, Openreach, Talk Talk Business and CityFibre, to ensure your business benefits from the best solution to match your needs. They also provide a 24/7 support service dedicated 24/7 monitoring and support and a customer portal for bandwidth usage reporting and incident management.
Our Dedicated Leased Lines offer ultrafast speeds which are dedicated to your business, meaning you don’t share the bandwidth with anyone else, ensuring that you can always rely on your connection.
Click the link below to read more about their features and benefits.
Features and Benefits – Dedicated Leased Lines
Are you looking for help in working out which leased line option best suits your business?
Get in touch, talk to one of our expert telecoms solutions team who develop best in class solutions solutions in collaboration with a range of highly regarded and proven global partners.
Team Challenge for Action Mental Health
General fundraising has been hit very hard by the COVID-19 pandemic. Thousands of fundraising events have been cancelled and many charities, are struggling to maintain services because of this huge reduction in income.
We believe that mental health is important as physical health and our charity champions have launched a TEAM CHALLENGE with a personal target, to raise funds and support our charity partner Action Mental Health.
This September everyone involved has agreed to complete 5k a day. The minimum distance will be covered by a variety of activities including walking, swimming, cycling and running.

Statistics on mental illness in Northern Ireland can be shocking, and experts believe they will be on the rise because of the impact of the recent pandemic.
Did you know?
- One in five adults in Northern Ireland will show signs of a mental illness
- NI had the 2nd highest rates of mental ill-health, when matched to 17 other countries.
Stress is a major factor and AMH have recently launched a tool to help people build resilience and get through difficult times. To find our more about the four A’s of Avoid, Alter, Adapt and Accept check out the guide to relieve stress and regain control: Steps to relieve pressure and regain control
Our team are committed to doing what we can to help support the vital work of the charity across Northern Ireland. Who offer a range of support services including:
- Mental Health Awareness
- Education & Training Schools Programs
- Young People Personal Development & Support
- Eating Disorders Learning, Disability Mental Health in the Workplace
- Advice Counselling and much more.
Help us to support the vital work of all at AMH by visiting our JustGiving Page and making a donation today.
All support and donations are greatly appreciated.

Effective Communication Is Essential For Success and Growth.
Ongoing restrictions impact our ability to live the life we knew a few months ago. But with change there is always opportunity.
How and when we communicate has been transformed and many companies have responded to change by implementing technology to enable their staff to adapt quickly to more remote or hybrid ways of working.
Effective communication is essential for success and growth of every organisation.
Is it time for you to get curious about technology?
We believe in strength in partnership and are proud to work with a range of global technology suppliers to ensure our customers have access a range of collaboration tools and technology services which can streamline the employee and customer experience. These include two of the biggest technology companies in the communication and collaboration marketplace, 8×8 and Microsoft.
Did you know?
- Your employees can collaborate on any device, across the entire organisation, even when they are on the move or scattered across the globe.
- You can have peace of mind with the highest level of security and compliance requirements in place.
- Your teams can connect and collaborate as if they were in the same room using HD video conferencing.
- You can decide which is best for you. There are video, voice and chat options available to allow you to empower your customers and employees to communicate however they want.
During this time of massive upheaval and constant change, people want to work with and for business’ they can trust. Communication within teams and customers provides reassurance in tough times.
Remote working has become a bigger motivator for staff during the past five years. All signs suggest this trend will only continue to grow and that remote teams are the future of work.

With almost half of the UK population already working remotely stats would suggest that many would like it to continue, or at least have the option of some days at home.
A Gallup study of US workers found that 59% of those surveyed would like to continue working remotely.
This means a new kind of communications and approach is required to ensure employees benefit from better work life balance and do not feel disengaged or isolated. In turn the business will benefit from increased productivity, a reduction in employee turnover rates and decrease in overhead costs.
Technology can help promote meaningful interactions internally and externally.
Customers expectations are at an all time high and business communication is vital, as a positive customer experience is immensely reliant on communication.
IT is personal, every business has different needs and it is important to ensure you work with a technology partner you can trust to help you find the right solutions to assist your business to perform beyond expectations and communicate effectively.
Get in touch today to talk to one of our expert team about the range of technology services and solutions we offer. We are here and would be happy to help. Or check out this video of a short break out session hosted at our recent virtual event which focused on communications to find out more.
A recent project by our team for Kingspan Water & Energy Limited involved unifying communications to improve their customer experience and employee engagement, read more about their experience with our team by clicking here
Can IT Maximise Your Business Performance?
In the age of Covid-19, Device Maintenance is on many business’s minds. IT Performance, Data Recovery and Data Security are just a few of things that business leaders could be concerned about in the current situation.
Legacy infrastructure lacks the modern technologies required to support the demands of the ever-changing technologies, increased traffic, distributed data, complicated security and compliance needs, and other necessities for effective IT infrastructures.
They are also placing game-changing demands on existing networks.

Network transformation isn’t just needed: it’s inevitable. But the capital outlay required for a network overhaul causes many organisations to think it’s impossible. However, based on our experience with our customers, we can always find a way to help. Our range of services can be tailor-made to ensure they offer the best fit solution for your business needs.
The longer you wait, the less you gain
Delaying inevitable projects, such as the provisioning of Data Security, Disaster Recovery and Device Management, means your business waits longer to realise the value of transformation, and that value shrinks in the interim.
You don’t have to build your network transformation alone
We’re dedicated to helping our customers overcome any of challenges brought by the recent pandemic, our certified teams are innovative in their approach. To meet our customer needs we develop best in class solutions using a diverse range of highly regarded and proven global partners, to ensure our customers have access to the most advanced range of services and solutions available.
Whilst there is a lot of uncertainty of what the future will look like researchers believe the COVID-19 crisis is likely to significantly accelerate the shift to digital and fundamentally shake up the business landscape.
We are here and ready to help you build a transformation road map for your business that will deliver positive results.
Click here to check out a video of a breakout session at our recent RE:IMAGINE virtual event, hosted by Jonny & Barry. Watch and listen as the guys discuss ideas and share information on how technology could help improve your overall business performance.
Get in touch to discuss your business needs with one of our expert team today.
Think Bigger
Digitalisation puts Information Technology at the centre of business growth. Now is the perfect time for business’ to respond to changes, forced by the recent pandemic, with technology solutions.
Along with recovery it is imperative that companies think bigger, beyond the current situations and reinvent or re:imagine a new way forward. Senior business leaders must address company pain points and frustrations by encouraging open dialogue and listening to their teams.
Then respond by working with an IT Consultant and IT company they can trust.
Together they can develop a business relationship to ensure everyone involved has a complete understanding of current business objectives and future plans. To allow expert teams involved in creating business transformation options and ideas to deliver best fit technology solutions from a range of local and Global Partners.
Cloud, VoiP, SaaS, VPN, MFA , the list of services can be mind numbing. The tech world is full of acronyms and a range of services that are vast and different, one size does not fit all. But the correct technology solution, created with your business in mind can:
- Enable innovation
- Secure Information
- Inspire customer confidence
- Create a next-generation workforce
- Facilitate collaboration
- Support flexibility
- Accelerate Growth
Technology is an enabler, working with the right IT provider is critical to your business success. Our expert teams are made up of the best people ready to engage in dialogue, create ideas, develop solutions, implement services and deliver results that will MAKE LIFE BETTER for you and your business.
Talk to us about how we can help you begin, develop or expand your business transformation journey.
But cybercriminals are adapting too. They’re placing fraudulent adverts on Google that mimic legitimate businesses, with one crucial difference: fake contact details. A victim searching for urgent help – a breakdown service, airline ticket support, or a last-minute hotel booking – might unwittingly call a scammer instead of the real company. These criminals exploit stressful situations, tricking people into handing over login credentials, financial information, or other sensitive details.
Google works hard to tackle fraudulent advertising, but the scale is vast, with over 14.5 billion ads investigated in 2023.
A simple defence? Scroll past the sponsored adverts and check website addresses carefully. If something feels off, verify phone numbers through independent sources and avoid giving personal information over the phone. Never trust an incoming call – always make the call yourself using a verified number.
Stay sharp online. The scammers are clever, but you can be smarter. 🔍
To find out how we can protect your business, contact us: 📞 028 9448 5112 ✉️ info@osgroup.co.uk 🌐 www.osgroup.co.uk